by titanadmin | Nov 30, 2017 | Email Scams, Phishing & Email Spam, Spam Advice, Spam News, Spam Software, Website Filtering |
Black Friday deals and Cyber Monday discounts see consumers head online in droves looking for bargain Christmas presents, but each year many thousands of consumers are fooled by holiday season email scams. This year will be no different. Scammers are already hard at work developing new ruses to fool unwary online shoppers into parting with their credentials or installing malware.
In the rush to purchase at discounted rates, security awareness often goes out the window and cybercriminals are waiting to take advantage. Hidden among the countless emails sent by retailers to advise past customers of the latest special offers and deals are a great many holiday season email scams. To an untrained eye, these scam emails appear to be no different from those sent by legitimate retailers. Then there are the phishing websites that capture credentials and credit card numbers and websites hosting exploit kits that silently download malware. It is a dangerous time to be online.
Fortunately, if you take care, you can avoid holiday season email scams, phishing websites, and malware this holiday period. To help you stay safe, we have compiled some tips to avoid holiday season email scams, phishing websites and malware this festive period.
Tips to Keep You Safe This Holiday Season
In the run up to Christmas there will be scams aplenty. To stay safe online, consider the following:
Always carefully check the URL of websites before parting with your card details
Spoofed websites often look exactly like the genuine sites that they mimic. They use the same layouts, the same imagery, and the same branding as retail sites. The only thing different is the URL. Before entering your card details or parting with any sensitive information, double check the URL of the site and make sure you are not on a scam website.
Never allow retailers to store your card details for future purchases
It is a service that makes for quick purchases. Sure, it is a pain to have to enter your card details each time you want to make a purchase, but by taking an extra minute to enter your card details each time you will reduce the risk of your account being emptied by scammers. Cyberattacks on retailers are rife, and SQL injection attacks can give attackers access to retailer’s websites – and a treasure trove of stored card numbers.
Holiday season email scams are rife – Be extra vigilant during holiday season
While holiday season email scams used to be easy to detect, phishers and scammers have become a lot better at crafting highly convincing emails. It is now difficult to distinguish between a genuine offer and a scam email. Emails contain images and company branding, are free from spelling and grammatical errors, and the email requests are highly convincing. Be wary of unsolicited emails, never open email attachments from unknown senders, and check the destination URL of any links before clicking.
If a deal sounds too good to be true, it probably is
What better time than holiday season to discover you have won a PlayStation 4 or the latest iPhone in a prize draw. While it is possible that you may have won a prize, it is very unlikely if you haven’t actually entered a prize draw. Similarly, if you are offered a 50% discount on a purchase via email, there is a high chance it is a scam. Scammers take advantage of the fact that everyone loves a bargain, and never more so than during holiday season.
If you buy online, use your credit card
Avoid the holiday season crowds and buy presents online, but use your credit card for purchases rather than a debit card. If you have been fooled by a holiday season scam or your debit card details are stolen from a retailer, it is highly unlikely that you be able to recover stolen funds. With a credit card, you have better protections and getting a refund is much more likely.
Avoid HTTP sites
Websites secured by the SSL protocol are safer. If a website starts with HTTPS it means the connection between your browser and the website is encrypted. It makes it much harder for sensitive information to be intercepted. Never give out your credit card details on a website that does not start with HTTPS.
Beware of order and delivery confirmations
If you order online, you will no doubt want to check the status of your order and find out when your purchases will be delivered. If you recent an email with tracking information or a delivery confirmation, treat the email as potentially malicious. Always visit the delivery company’s website by entering in the URL into your browser, rather than clicking links sent via email. Fake delivery confirmations and parcel tracking links are common. The links can direct you to phishing websites and sites that download malware, while email attachments often contain malware and ransomware downloaders.
Holiday season is a busy, but take your time online
One of the main reason that holiday season email scams are successful is because people are in a rush and fail to take the time to read emails carefully and check attachments and links are genuine. Scammers take advantage of busy people. Check the destination URL of any email link before you click. Take time to think before you take any action online or respond to an email request.
Don’t use the same password on multiple websites
You may choose to buy all of your Christmas gifts on Amazon, but if you need to register on multiple sites, never reuse your password. Password reuse is one of the easiest ways that hackers can gain access to your social media networks and bank accounts. If there is a data breach at one retailer and your password is stolen, hackers will attempt to use that password on other websites.
Holiday season is a time for giving, but take care online and when responding to emails to make sure your hard-earned cash is not given to scammers.
by titanadmin | Nov 30, 2017 | Email Scams, Network Security, Phishing & Email Spam, Spam News |
A spam email campaign has been detected that is distributing a form of Cobalt malware. The attackers use the Cobalt Strike penetration testing tool to take full control of an infected device. The attack uses an exploit for a recently patched Microsoft Office vulnerability.
The spam emails appear to have been sent by Visa, informing the recipient about recent changes to its payWave service. The emails contain a compressed file attachment that is password-protected. The password required to extract the contents of the zip file is contained in the body of the email.
This is an apparent attempt to make email recipients believe Visa had included security controls to prevent unauthorized individuals from viewing the information in the email – a reasonable security measure for a financial communication. Also contained in the email is a RTF file that is not password protected. Opening that file will launch a PowerShell script that will download a Cobalt Strike client that will ultimately give the attackers full control of the infected device.
The attackers leverage a vulnerability in Microsoft Office – CVE-2017-11882 – which was patched by Microsoft earlier this month. The attackers use legitimate Windows tools to execute a wide range of commands and spread laterally across a network.
The campaign was detected by researchers at Fortinet, who report that by exploiting the Office flaw, the attackers download a Cobalt Strike client and multiple stages of scripts which are then used to download the main malware payload.
The flaw has existed in Office products for 17 years, although it was only recently detected by Microsoft. Within a few days of the vulnerability being detected, Microsoft issued a patch to correct the flaw. Within a few days of the patch being released, threat actors started leveraging the vulnerability. Any device that has a vulnerable version of Office installed is vulnerable to attack.
This campaign shows just how important it is for patches to be applied promptly. As soon as a vulnerability is disclosed, malicious actors will use the vulnerability in attacks. When patches are released, malicious actors get straight to work and reverse engineer the patch, allowing them to identify and exploit vulnerabilities. As these attacks show, it may only take a few hours or days before vulnerabilities are exploited.
The recent WannaCry and NotPetya malware attacks showed just how easy it is for vulnerable systems to be exploited. Both of those attacks leveraged a vulnerability in Windows Server Message Block to gain access to systems. A patch had been released to address the vulnerability two months before the WannaCry ransomware attacks occurred. Had patches been applied promptly, it would not have been possible to install the ransomware.
Protecting against this Cobalt malware campaign is straightforward. Users simply need to apply the Microsoft patch to prevent the vulnerability from being exploited. Using a spam filter such as SpamTitan is also recommended, to prevent malicious emails from reaching end users’ inboxes.
by titanadmin | Nov 29, 2017 | Email Scams, Network Security, Phishing & Email Spam, Spam News |
Millions of spam emails containing Scarab ransomware have been detected over the past few days. The massive spam campaign is being conducted using the Necurs botnet – one of the largest botnets currently in use.
The Necurs botnet has been active for at least five years and now contains more than 6 million zombie computers that are used to send masses of spam emails. Necurs has previously been used to send banking Trojans and many other forms of malware, although recently, the operators of the botnet have turned to spreading ransomware, including Locky.
The latest campaign saw the Necurs botnet send out spam emails to more than 12.5 million email accounts in the space of just 6 hours, with individuals in the United States, France, Germany, Australia, and the UK targeted.
The emails were typical of other phishing campaigns conducted in recent months. The emails appear to have been sent from well known, trusted brands to increase the likelihood of the malicious attachments being opened. This campaign spoofs printer manufacturers such as HP, Canon, Lexmark and Epson.
The emails contain a 7zip file attachment which claims to be a scanned document, with the subject line “Scanned from [Printer company]. The zip file contains a VBScript which, if run, will download Scarab ransomware.
Scarab ransomware is a relatively new ransomware variant, first detected over the summer. While most ransomware variants have a fixed price for obtaining the key to unlock the encryption, the authors of Scarab ransomware do not ask for a specific amount. Instead, the ransom payment depends on how quickly the victim responds.
As with the NotPetya wiper, users are required to make contact with the attackers via email. This method of communication has caused problems for victims in the past, as if the domain is taken down, victims have no method of contacting the attackers. In this case, an alternative contact method is provided – victims can also contact the attackers via BitMessage.
Even though Scarab ransomware is unsophisticated, it is effective. There is no free decryptor available to recover files encrypted by Scarab ransomware. Recovery without paying the ransom is only possible if backups of the encrypted files exist, and if the backup has not also been encrypted.
Scarab ransomware is believed to be the work of relatively small players in the ransomware arena. However, the scale of the campaign and the speed at which the spam emails are being sent shows that even small players can conduct massive, global ransomware campaigns by teaming up with the operators of botnets.
By using ransomware-as-a-service, anyone can conduct a ransomware campaign. Ransomware can be hired on darknet forums for next to nothing and used to extort money from businesses. More players mean more ransomware attacks, and the ease of conducting campaigns and the fact that many victims pay up, mean ransomware is still highly profitable.
Security experts are predicting that 2018 will see even more ransomware attacks. AV firm McAfee has predicted that next year will see cybercriminal gangs step up their attacks and target high-net worth individuals and small businesses, while the campaigns will become more sophisticated.
With the threat likely to increase, businesses need to ensure that they have solutions in place to prevent ransomware from being delivered to end users. By implementing an advanced spam filtering solution, businesses can ensure that phishing and spam emails do not get delivered to end users, mitigating the threat from ransomware. Fail to block malicious emails, and it will only be a matter of time before an employee responds, opens an infected email attachment, and installs ransomware on the network.
If you are looking for the best spam filter for business use, contact the TitanHQ team today for further information on SpamTitan.
by titanadmin | Nov 20, 2017 | Email Scams, Internet Security, Network Security, Phishing & Email Spam, Spam Advice, Spam Software |
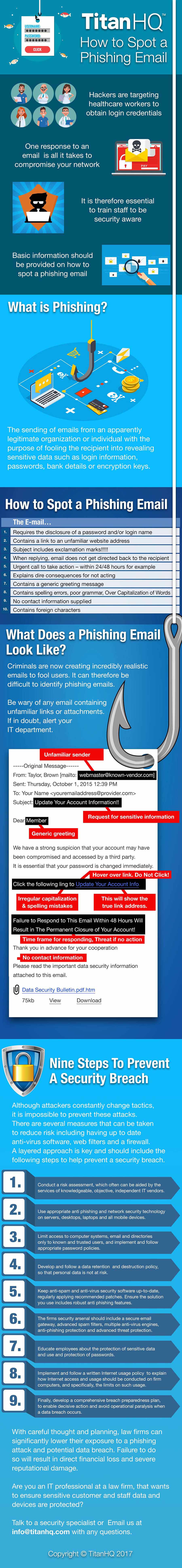
All organizations should take steps to mitigate the risk of phishing, and one of those steps should be training employees how to spot a phishing email. Employees will frequently have their phishing email identification skills put to the test.
Since all it takes is for one employee to fall for a phishing scam to compromise a network, not only is it essential that all employees are trained how to spot a phishing email, their skills should assessed post-training, otherwise organizations will not know how effective the training has been.
How Common are Phishing Attacks?
Phishing is now the number one security threat faced by businesses in all sectors. Research conducted by the security awareness training company PhishMe suggests that more than 90% of cyberattacks start with a phishing or spear phishing email. While all industry sectors have to deal with the threat from phishing, the education and healthcare industries are particularly at risk. They are commonly targeted by scammers and spammers, and all too often those phishing attacks are successful.
The Intermedia 2017 Data Vulnerability Report showed just how common phishing attacks succeed. Workers were quizzed on security awareness training and successful phishing attacks at their organizations. 34% of high level execs admitted falling for a phishing scam, as did 25% of IT professionals – Individuals who should, in theory, be the best in an organization at identifying phishing scams. The same study revealed 30% of office workers do not receive regular security awareness training. 11% said they were given no training whatsoever and have not been taught how to spot a phishing email.
Overconfidence in Phishing Detection Capabilities Results in Data Breaches
Studies on data breaches and cybersecurity defenses often reveal that many organizations are confident in their phishing defenses. However, many of those companies still suffer data breaches and fall for phishing attacks. Overconfidence in phishing detection and prevention leaves many companies at risk. This was recently highlighted by a study conducted by H.R. Rao at the University of Texas at San Antonio. Rao explained that many people believe they are smarter than phishers and scammers, which plays into the scammers’ hands.
Training Should be Put to The Test
You can train employees how to spot a phishing email, but how can you tell how effective your training has been? If you do not conduct phishing simulation exercises, you cannot be sure that your training has been effective. There will always be some employees that require more training than others and employees that do not pay attention during training. You need to find these weak links. The best way to do that is with phishing simulation exercises.
Conduct dummy phishing exercises and see whether your employees are routinely putting their training into action. If an employee fails a phishing test, you can single them out to receive further training. Each failed simulation can be taken as a training opportunity. With practice, phishing email identification skills will improve.
How to Spot a Phishing Email
Most employees receive phishing emails on a daily basis. Some are easy to identify, others less so. Fortunately spam filters catch most of these emails, but not all of them. It is therefore essential to train employees how to spot a phishing email and to conduct regular training sessions. One training session a year is no longer sufficient. Scammers are constantly changing tactics. It is important to ensure employees are kept up to speed on the latest threats.
During your regular training sessions, show your employees how to spot a phishing email and what to do when they receive suspicious messages. In particular, warn them about the following tactics:
Spoofed Display Names
The 2017 Spear Phishing Report from GreatHorn indicates 91% of spear phishing attacks spoof display names. This tactic makes the recipient believe the email has been sent from a trusted colleague, friend, family member or company. This is one of the most important ways to spot a phishing email.
Mitigation: Train employees to hover their mouse arrow over the sender to display the true email address. Train employees to forward emails rather than reply. The true email address will be displayed.
Email Account Compromises
This year, business email compromise (BEC) scams have soared. These scams were extensively used to obtain W-2 Form tax information during tax season. This attack method involves the use of real email accounts – typically those of the CEO or senior executives – to send requests to employees to make bank transfers and send sensitive data.
Mitigation: Implement policies that require any email requests for sensitive information to be verified over the phone, and for all new bank transfer requests and account changes to be verified.
Hyperlinks to Phishing Websites
The Proofpoint Quarterly Threat Report for Q3 showed there was a 600% increase in the use of malicious URLs in phishing emails quarter over quarter, and a 2,200% increase from this time last year. These URLs usually direct users to sites where they are asked to login using their email credentials. Oftentimes they link to sites where malware is silently downloaded.
Mitigation: Train employees to hover their mouse arrow over the URL to display the true URL. Encourage employees to visit websites by entering the URL manually, rather than using embedded links.
Security Alerts and Other Urgent Situations
Scammers want email recipients to take action quickly. The faster the response the better. If employees stop and think about the request, or check the email carefully, there is a high chance the scam will be detected. Phishing emails often include some urgent request or immediate need for action. “Your account will be closed,” “You will lose your credit,” “Your parcel will not be delivered,” “Your computer is at risk,” Etc.
Mitigation: Train employees to stop and think. An email request may seem urgent and contain a threat, but this tactic is commonly used to get people to take quick action without engaging their brains.
Look for Spelling Mistakes and Grammatical Errors
Many phishing scams come from African countries, Eastern Europe and Russia – Places where English is not the main language. While phishing scams are becoming more sophisticated, and more care is taken crafting emails, spelling mistakes and poor grammar are still common and are a key indicator that emails are not genuine.
Mitigation: Train employees to look for spelling mistakes and grammatical errors. Companies check their emails carefully before sending them.
Why a Spam Filter is Now Essential
Training employees how to spot a phishing email should be included in your cybersecurity strategy, but training alone will not prevent all phishing-related data breaches. There may be a security culture at your organizations, and employees skilled phish detectors, but every employee can have an off day from time to time. It is therefore important to make sure as few phishing emails as possible reach employees’ inboxes, and for that to happen, you need an advanced spam filtering solution.
SpamTitan blocks more than 99.9% of spam email and includes dual anti-virus engines to ensure malicious messages are blocked. The low false positive rate also ensures genuine emails do not trigger the spam filter and are delivered.
If you want to improve your security defenses, train employees how to spot a phishing email and implement SpamTitan to stop phishing emails from reaching inboxes. With technological and human solutions you will be better protected.
Handy Infographic to Help Train Staff How to Spot a Phishing Email
We have compiled a useful infographic to highlight how important it is to train staff how to spot a phishing email and some of the common identifiers that an email is not genuine:
by titanadmin | Nov 17, 2017 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
The Ponemon Institute has published the findings of a new report on endpoint security risk, which shows that ransomware attacks have occurred at most companies, the risk of fileless malware attacks has increased significantly, and successful cyberattacks are resulting in average losses of more than $5 million.
For the Barkly-sponsored endpoint security risk study, the Ponemon Institute surveyed 665 IT security professionals that were responsible for the management of their organization’s security risk.
7 out of ten respondents claimed endpoint security risk was significantly higher this year than in 2016, and one of the biggest threats was now fileless malware. Companies are still using traditional anti-virus and anti-malware solutions, although they are not effective at preventing fileless malware attacks.
Fileless malware is not detected by most anti-virus solutions since no files are written to the hard drive. Instead, fileless malware remains in the memory, oftentimes leveraging legitimate system tools to gain persistence and spread to other devices on the network.
These fileless malware attacks are occurring far more frequently, with respondents estimating a 20% rise in attacks in 2017. 29% of all cyberattacks in 2017 involved fileless malware, and the threat is expected to continue to increase, and will account for more than a third of all attacks in 2018.
The switch from file-based malware to fileless malware is understandable. The attacks are often successful. 54% of companies surveyed said they had experienced at least one cyberattack that resulted in data being compromised, and 77% of those attacks involved exploits or fileless malware. 42% of respondents said they had experienced a fileless malware attack that resulted in systems or data being compromised in 2017.
Fileless malware attacks are increasing, but so are ransomware attacks. Over half of companies that took part in the endpoint security risk study said they had experienced at least one ransomware attack in 2017, while four out of ten firms experienced multiple ransomware attacks. Even though most companies backup their files, 65% of respondents said they had paid a ransom to recover their data, with the average amount being $3,675. The primary method of ransomware delivery is email.
While the ransom payments may be relatively low, that represents only a small proportion of the costs of such attacks. For the endpoint security risk study, firms were asked to estimate the total cost of cyberattacks – On average, each successful attack on endpoints cost an average of $5,010,600 to resolve – $301 per employee.
Protect Against Malware Attacks by Blocking the Primary Delivery Vector
Email is the primary method for distributing malware. Implementing a spam filtering solution, preferably a gateway solution, can keep an organization protected from malicious emails and will prevent malicious messages from being delivered to end users, and is important for helping organizations manage endpoint security risk.
Many companies opt for an email gateway filtering appliance – an appliance located between the firewall and email server. These solutions are powerful, but they come at a cost since the appliance must be purchased. These appliance-based solutions also lack scalability.
If you want the power of an appliance, but want to keep costs to a minimum, consider a solution such as SpamTitan. SpamTitan offers the same power as a dedicated appliance, without the need to purchase any additional hardware. SpamTitan can be deployed as a virtual appliance on existing hardware, offering the same level of protection as an email gateway filtering appliance at a fraction of the cost.
Don’t Forget to Train Your Employees to be More Security Conscious
A recent InfoBlox survey on healthcare organizations in the United States and United Kingdom revealed that companies in this sector are realizing the benefits of training employees to be more security aware, although only 35% of firms currently provide training to employees.
No matter what email filtering solution you use, there will be times when spammers succeed, and messages are delivered. It is therefore important that staff are trained how to identify and respond to suspicious emails. If end users are not aware of the threats, and do not know how to recognize potential phishing emails, there is a higher chance of them engaging in risky behavior and compromising their device and the network.

