Spam presents a widespread problem, affecting revenue, causing data breaches, and posing a significant inconvenience for administrators and users alike. Without a spam filter, users can receive hundreds of spam messages daily depending on their email address visibility across the internet. Publicly accessible email services have their spam filters, but users still have access to a spam box, leaving them vulnerable to attacks. Business-level email services like Microsoft Office 365 also have spam filtering services, which must be more sophisticated to stop attacks.
The Daily Spam Nuisance
It’s estimated that 8 billion spam emails are sent globally every day. Some of these emails are ads, others are advertisements for illicit sales, and some are used for malicious purposes like malware. Although most people see spam as a nuisance, it’s also costly for businesses. Keeping email messages in a spam box increases storage costs, and allowing messages to reach users increases the risks of phishing and data breaches.
Individuals can rely on free email services to handle spam, but businesses need a better solution. With 8 billion spam emails sent daily, storing messages adds an unnecessary cost. The trick is automatically dropping spam emails and removing them from business system storage but avoiding false positives. A false positive interrupts communication frustrates employees and can cost money should the business spam filter block critical messages.
If you’ve ever looked at your personal email spam box, you also know that spammers change their strategies to bypass filters. The same happens with enterprise email systems. You might have a currently effective spam filtering solution, but it will likely be ineffective in the future. Businesses need a spam filtering solution that changes as spammers change their bypass strategies. Enterprise businesses have higher stakes, as a single bypass could lead to a data breach. The aftermath of a data breach can last for years, and a single data breach costs businesses millions in compliance violations, litigation, and brand damage.
What Types of Spam Affect Businesses?
When anyone mentions email spam, your thoughts include images of nuisance messages selling illicit products. While this type of spam is common, there are other types of spam organizations must stop from clogging up their systems. Spam comes in many forms, and the people who send it also have several strategies to bypass filters. Here are a few more spam types that shouldn’t reach recipient inboxes:
- Financial scams: Most people know about “Nigerian prince” email scams, but the strategy comes in many forms. The sender promises a large sum of money in exchange for a small transaction fee. For example, the sender promises a share in monetary winnings if the recipient pays shipping fees.
- Investment scams: Scammers prey on victims desperate for money. The “get rich quick” strategy involves sending Bitcoin to a scammer, who promises significant returns on the victim’s investment. Bitcoin transactions cannot be reversed, so the victim loses the money without any way to get it back.
- Phishing: Not all spam is harmless. Some spam messages carry malicious intent. Phishing is the primary attack strategy for malware delivery, credential theft, and data theft. Most phishing attacks target specific people within the organization, and it’s one of the most important reasons for email security and filters.
- Adware: Email messages disguised as ads trick users into opening a website and downloading malware. Ransomware is often distributed using this method, or an attacker might attach a file to run macros that download and install ransomware. Not every ad network ensures their viewers’ safety and often allows advertisers to distribute malware.
- Message spam: Employees with access to social media (e.g., corporate social media managers) are vulnerable to message spam. Spammers scour Facebook, Twitter, Instagram, and LinkedIn for corporate targets. Spammers might target specific corporate individuals to trick them into sending money or convince targets to download malware.
- Comment spam: Similar to message spam, spammers use commenting systems to spread their ads and malicious links. Any business blog is vulnerable to comment spam, which also affects social media accounts. Organizations should train employees to identify malicious links and pages, but web content filters work with email security to stop users from accessing malicious URLs.
- Pingback spam: Some businesses have alerts to send a message when the brand is mentioned on social media or a public website. The pingback contains a link to a phishing site or possibly a simple trick to get the victim to pay money to the attacker. Users with corporate cards or access to financial data could be targets for this type of spam.
- Browser notification spam: When users visit a website, they might be asked to allow the site to send notifications to the browser. The browser then shows the notification on the user’s desktop. This notification system can be used maliciously when the attacker displays messages to bring users to a phishing page or a page asking for payments.
While many of the above spam methods work with browser interaction, most involve email messages with malicious links. The best solution is to use email filters and web browsing technologies to block users from participating in fraudulent spam activity. At the very least, email filters are the single most important first defense in email-based threats. Security awareness training is also beneficial but should only be used as a failsafe when email filters throw a false negative.
How Spam Messages Work on Vulnerable Employees
Many people wonder how anyone would fall for such an apparent attack after an email-based attack. Strategies used in email-based attacks often play on human emotion, mainly a sense of urgency to disregard all security awareness training and critical thinking. For example, a spam message might contain a message from a sender claiming to be the recipient’s boss. The sender tells the recipient to send money, perform an action quickly, or risk losing their job.
Too much spam also works to slow down employees. Employee productivity affects overall revenue. Too much time reading and removing spam manually takes too much employee time and can interfere with normal job activities. For example, if a sophisticated attack bypasses ordinary email filters, employees might question the legitimacy of a message. To determine if the message is legitimate, the employee might email another employee, their boss, or an IT person for help. Not only does this activity take up the recipient’s time, but it also takes time for other employees to investigate the message’s legitimacy. This example covers one message, but imagine a large enterprise with thousands of employees also dealing with spam messages. Calculating the time and revenue loss from spam messages could result in millions of dollars lost in chasing spam messages.
Fail safes are necessary in an enterprise organization, but spam messages work to bypass all security as best as possible. In a sophisticated attack, the sender might use social engineering in addition to malicious email messages. Dual attacks using spam and social engineering are often carried out by organized cybercriminals located in other countries. They have practice and the people available to perform multiple actions, and they will continue to find ways to trick employees even after the first attempts fail.
Recently, cyber-criminals have turned to spam, threatening small businesses with blackmail. Spammers demand money from companies to stop them from harassing customers and their competitors. The threats include sending malicious messages to website owners using their contact forms, sending advertisements implicating the target business as scam advertisers, and spamming forums with the company URL to get the victim company on global spam lists. Essentially, the spammers threaten the victim company with a damaging reputation assault online unless the business pays them.
Increased Spam Activity Targeting Office 365 Users
Spam affects everyone—businesses, individuals, adults, kids, everyone. Cybercriminals target businesses for their much bigger pockets, which means they can potentially get seven-figure payouts for their efforts. This does not mean individuals are free from being targets. They, too, can be victims, but businesses can afford six—and seven-figure payouts, while most individuals can barely afford four figures.
Enterprise businesses use email solutions, and Microsoft Office 365 is a standard system integrated into the environment. Cyber-criminals create malware and email-based threats targeting the most common systems to hedge their bets. Office 365 integrates with storage, email, productivity software, and other employee applications. A single bypass could allow an attacker to embed malware into the environment. Sophisticated malware stays stealthy and remains in the environment for as long as possible, potentially months.
Cybercriminals will create an email to spoof DocuSign as an example of an Office 365 targeted attack on businesses. DocuSign is a popular e-signing application where you receive an email request to sign a document. Before signing the document, recipients are asked to authenticate if they have an account. The DocuSign link is a phishing page used to collect victim passwords. An employee falling for the phishing attempt gives attackers their password without realizing it.
The next step is to steal the victim’s business email account. Business email compromise (BEC) is a common next step in phishing. It gives attackers a higher level of account access to the business system. Usually, the attacker knows that a corporate staff member signing legal documentation also has access to high-privilege data. With access to the business email account, the attacker can scan for important information, including other accounts – financial accounts, corporate infrastructure credentials, or other high-privilege accounts where it could be financially beneficial to compromise.
With enough permissions on an account, an attacker can create new financial accounts like a credit card and send the card to their address. An accountant’s email could transfer money from the business bank account to the attacker’s. Private data such as employee social security numbers could be stolen if the attacker compromises an HR executive’s account. Even a low-privilege account can scan the network for private data or gain access to customer information. Customer emails could be used to perform additional phishing attacks, or stolen customer data could be used for identity theft.
The DocuSign phishing scam is just one strategy targeting Office 365, but cyber-criminals have numerous others available. Office 365 has security to catch some of these spam emails but cannot catch targeted attacks. Microsoft’s security technology is built for the masses, so it’s unable to account for email-based attacks targeting specific businesses and industries. Businesses need additional security to protect their particular infrastructure, standard industry procedures, and corporate staff.
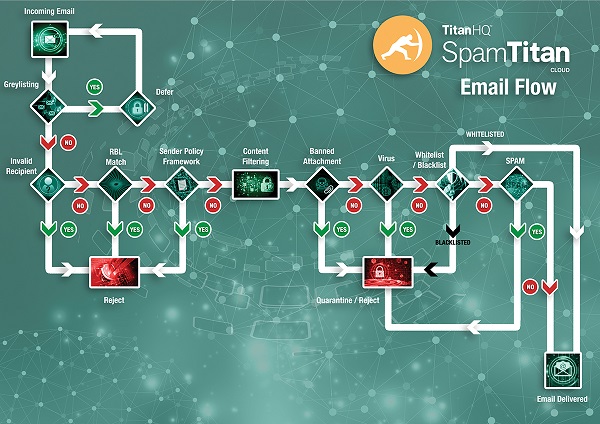
Email Filtering for Office365
SpamTitan for Office 365 allows you supplement Office 365s native email security with award-winning phishing protection from a dedicated security provider. SpamTitan’s sandboxing feature protects against breaches and sophisticated email attacks by providing a powerful environment to run in-depth, sophisticated analysis of unknown or suspicious programs and files. SpamTitan for Office 365 adds more advanced security like protection from phishing and spear phishing, including Business Email Compromise and zero-day protection.
SpamTitan email filtering incorporates numerous features designed to complement the spam filter on Office 365, including:
- SpamTitan focuses on a defense in depth approach protecting against malware threats, spear phishing attempts, and zero-day attacks.
- Predictive techniques such as Bayesian analysis, heuristics, and machine learning to preemptively block emerging forms of spear phishing, whaling, and zero-day attacks before they infiltrate your mailbox.
- Implementation of heuristic rules to identify phishing attempts based on message headers and other indicators, with regular updates to combat evolving threats.
- Rapid deployment
- Seamless integration with Active Directory, Azure AD, and LDAP for effortless synchronization.
- Administration facilitated through a user-friendly web-based portal, eliminating the need for additional agents.
- Flexible application of Spam Confidence Levels at the user, user-group, and domain levels.
- Capability to whitelist or blacklist senders and IP addresses to fine-tune security measures. SpamTitan is infinitely scalable and universally compatible.
Sandboxing
- SpamTitan sandboxing offers robust protection against breaches and data loss caused by zero-day threats. It creates a secure environment to conduct thorough analysis of unknown or suspicious programs and files, protecting against potential vulnerabilities.
- SpamTitan safeguards against malware, spear-phishing, and advanced persistent threats (APTs). SpamTitan sandboxing not only identifies new threats but also provides valuable insights to mitigate risks effectively.
The combination of these features ensures SpamTitan protects users and businesses, using Office 365 from whaling, spear phishing, impersonation attempts, and business email compromise (BEC) attacks.
Discover how SpamTitan stops Office 365 from becoming a haven for phishing messages. Sign up for a complimentary demo to see how SpamTitan uses cutting-edge intelligent technology to block sophisticated phishing attacks.
FAQs about Improving the Spam Filter on Office 365
Do I need to replace the Office 365 spam filter?
You do not need to replace the Office 365 spam filter to improve your protection against spam, phishing, and malware, you just need to layer an extra level of protection on top with a third-party solution to block more sophisticated spam and phishing emails.
SpamTitan for Office 365 allows you to supplement Office 365’s native email security with award-winning phishing protection from a dedicated security provider. As ransomware and phishing attacks increase, Office 365 has become a primary target, making it vital for IT professionals to take proactive steps with Office 365 email security and “hack-proof” their environments.
Will a spam filter detect compromised email accounts?
A spam filter can detect compromised email accounts if it is configured to scan outbound emails and rules are applied to detect spam, phishing signatures, malware, and attempts to send certain types of data outside the organization. Rule violations should trigger alerts for the security team, who will be able to determine whether an email account is compromised or not.
How does a spam filter block malware and ransomware?
A spam filter blocks malware and ransomware by checking URLs included in – or embedded into – each email against blacklists of known malware and ransomware. Some filters also support URL rewriting and time-of-click analysis to protect against links to websites that appear to be safe on delivery, but are later weaponized with malware.
What does defense in depth mean?
Defense in depth means implementing overlapping security layers to ensure that if one mechanism fails to provide protection, others exist to stop an attack succeeding. A defense in depth approach provides the key elements needed to secure assets: prevention, detection, and response. SpamTitan email security uses a defense in depth approach and incorporates many different detection mechanisms to block email threats.
How much does SpamTitan cost?
The best way to determine how much does SpamTitan cost is to use our cost calculator or contact our sales team for a no obligation quote. SpamTitan pricing is highly competitive, but it is not possible to give a general cost as the price depends on the number of users and the length of the license period.
Why is my business suddenly getting more spam emails?
If your business is suddenly getting more spam emails, it is likely your business email addresses have been recently harvested by a bot and added to a “mailing list”. If your mail filter is configured to the optimum settings, you can reduce the volume of spam evading detection by reporting spam emails to Microsoft and/or adding the spammer’s IP address to your business’s mail blacklist.
What is a sender policy framework?
A sender policy framework is an email authentication method which ensures the sending mail server is authorized to originate mail from the email sender’s domain. The reason sender policy frameworks are checked by email filters is to prevent spoofing – a threat that involves cybercriminals and spammers sending email messages with a fake sender address.
How does tagging prevent internal data loss?
Tagging prevents internal data loss when rules are applied to prevent specific types of data leaving the corporate network via email. When the outbound mail filter identifies tagged data in an outbound email, it will flag the event to the security team and usually hold the email until such time as the email is manually okayed – or blocked – by the security team.
Is it possible to block emails from specific locations?
It is possible to block emails from specific locations either by adding individual IP addresses to the mail blacklist – if, for example, you wanted to block spam emails from an individual source – or by geo-blocking an entire IP range. If you have contacts in the geo-blocked range, you can allow their emails to circumnavigate the mail filter by adding their IP addresses to the mail whitelist.
What is the optimal setting for a mail filter?
The optimal setting for a mail filter varies depending on the requirements of the organizations, the roles of individuals within the organization, and individual susceptibility to threats. Therefore, a finance organization is likely to use a mail filter with more aggressive optimal settings than a sales organization. Similarly, administrators may want to block all but whitelisted emails for individuals with access to sensitive information or who have shown themselves to be a risk to security.
