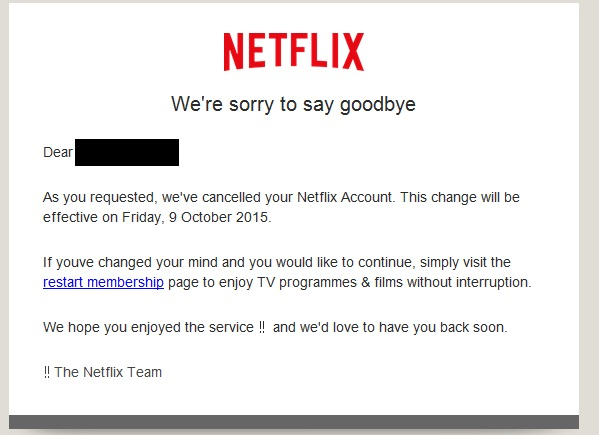
A new Netflix phishing scam has been uncovered which works by telling users their Netflix accounts have been closed, requiring action to regain access to the service. Doing so will give your confidential login details to the scam operators.
Netflix has 62.27 million users, making it a highly attractive target for email scammers and spammers, and consequently Netflix phishing scams are common.
Latest Netflix Phishing Scam Convinces users to Reveal their Account Details
Recipients of the fake Netflix emails are required to click a link in order to reactivate their accounts. Unknown to the victims of this Netflix phishing scam, clicking on the link will direct them to a fake Netflix page, and by reactivating their accounts they will be giving the scammers their account names, passwords, and potentially other sensitive information.
Unfortunately for Netflix users, revealing passwords for one account may also mean other online accounts are compromised. Many users share their passwords across different websites, often using the same or similar passwords for Netflix, Facebook, and a host of other sites, including online banking portals.
TitanHQ recommends Netflix users ignore the email and delete it, and certainly do not to click on the link in the email. Phishing scams such as this usually direct users to a website that has been infected with malware, and clicking the link will result in that malware being downloaded, even if no information is entered on the page.
The best course of action is to login to your Netflix account as you would normally do, by typing in the URL or using your bookmark, and check your account status directly with Netflix. In all likelihood, it will still be active.
Further Information on the New Netflix Phishing Scam
Below is a screenshot of the latest Netflix phishing scam. The email appears genuine enough, although close inspection will reveal a few grammatical errors, such as missing apostrophes and misplaced exclamation marks. However, the email could be enough to fool the unwary, and especially individuals who tend to skim read emails and click first and think later.
This phishing campaign is similar to others that have been recently sent to users of other online services. Phishing emails are devised to give the recipient a legitimate reason for handing over sensitive information, usually via webpage.
These include, but are not limited to:
- Upgrading security settings
- Performing essential system maintenance
- Verifying account details to prevent fraud
- Claiming a refund for a bill that has been paid
- Giving money back for an incorrect charge
- Offering you a free gift or service
Email scams often deliver malicious programs – malware – that has been created to steal confidential data such as account login names and passwords. Phishing campaigns are launched on social media, although email is the most common way that these scams are delivered.
Generally speaking, phishing campaigns can be categorized in three types:
Off-the-Shelf Jacking Toolkits
Criminals can purchase malware online which can be used to scam users into revealing passwords, which can subsequently be used to empty bank accounts, rack up debts, or hold people to ransom (the latter is becoming increasingly common and is referred to as ransomware). Once access is gained to an account or computer, Ransomware is used to encrypt data. The users are then required to pay a ransom to the perpetrator of the scheme in order to get their data unlocked.
These campaigns are usually opportunistic in nature, and involve millions of spam emails being sent. It is a numbers game, and some users will click on the phishing links and compromise their computers and networks.
Zero-day Vulnerability Exploits
The net is also cast similarly widely with these email phishing campaigns; however, the malware delivered is more complex, and the hackers behind these schemes are considerably more skilled. Zero-day vulnerabilities are new security flaws that have been discovered in software that have yet to be discovered by the software vendor. Consequently, patches do not exist to deal with the threat. Malware is created to exploit these vulnerabilities, which is usually delivered via an infected email attachment, although it can be downloaded when users visit a phishing website.
Spear Phishing Campaigns
These are targeted attacks that are conducted on individuals, or in some cases, organizations. The perpetrators of these schemes are skilled, and invest considerable time and effort into creating convincing campaigns. Oftentimes extensive information is gathered on the targets prior to the phishing emails being sent.
These schemes similarly use zero day vulnerabilities, and these advanced persistent threats (APT) have been used in a number of high profile attacks, such as the recent Carbanak malware attacks which have made the headlines recently.
How to Avoid Becoming a Phishing Victim
The best defense against attack is to be vigilant. Security awareness training for employees is essential. Staff members must be alerted to the risk, the consequences of clicking on a phishing link, and told how to identify scams. They should be instructed to check links before clicking (by hovering the mouse arrow over the link to check the real address).
It is also essential to keep all software patched and up to date. This applies to operating systems, applications, web browsers and other software. Software should be configured to update automatically wherever possible. Organizations should also develop concise patch management policies. Continuous security audits should be conducted and multi-layered network security controls developed.
There are a number of ways that spam and phishing emails can be prevented from being delivered to users, such as using a spam filter. Web filtering is particularly useful in prevent users from visiting known malware and phishing sites.