Many of our tips for reducing spam emails also serve the purpose of preventing malicious emails from being delivered – those containing malware or other email-borne threats.
Some of our anti-spam tips revolve around features that should be present in spam filters by default - but not all are. Others involve measures you can implement yourself. Consequently, it is your best interests to determine the mechanisms you already have in place to detect spam, and then adjust, add or replace as necessary.
No matter what email server or spam filter you’re using, there are a few quick and easy things you can do to reduce spam and related malware attacks on your network. Use the list below as a guide to important steps to take to protect your user from spam.
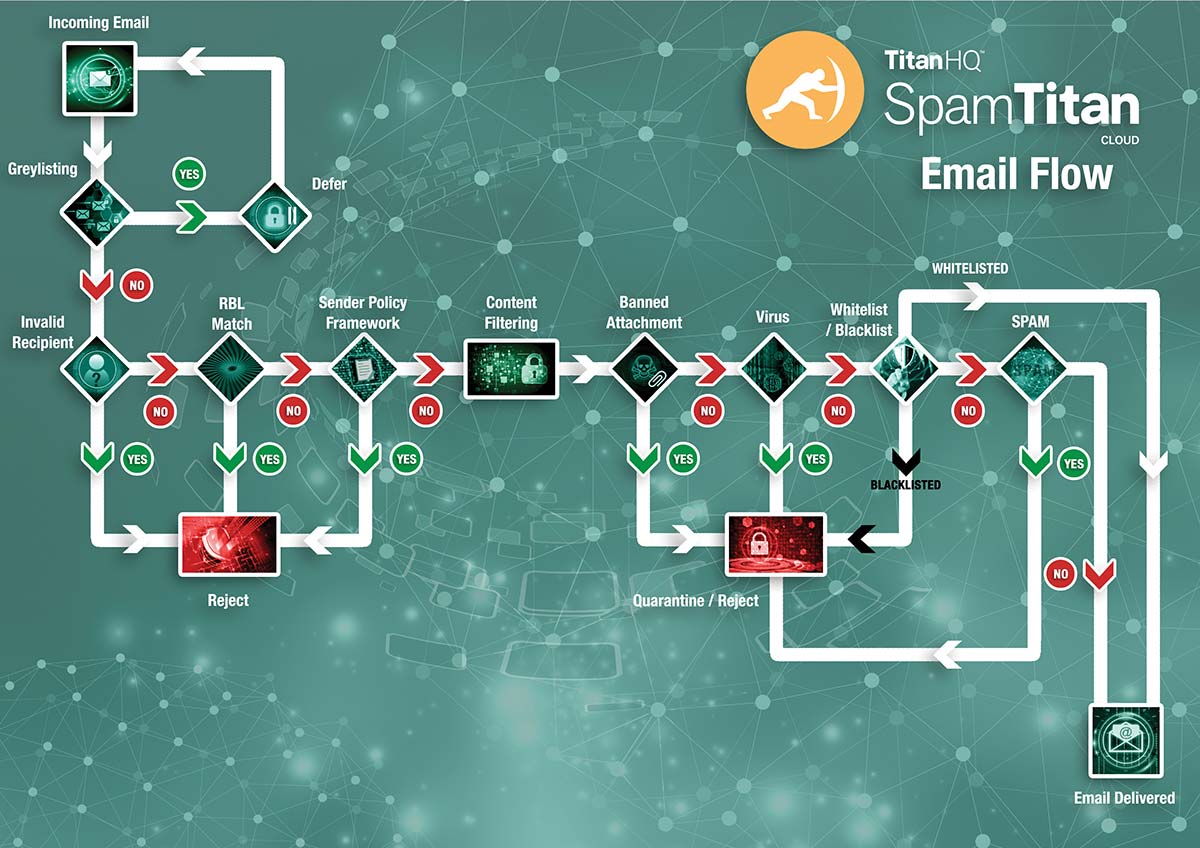
1. Make Sure the Filter´s Realtime Block List (RBL) Updates in Real Time
Whether or not you have implemented a third-party spam filter to protect your network, you will likely be using a Realtime Block List or RBL. A Realtime Block List is a blacklist containing the IP addresses of servers known to be used for sending spam emails and is present of every type of email filter from Outlook and Yahoo upwards.
The Realtime Block List compares every inbound email against the blacklist of known spam servers and rejects those that appear on the list. Typically, the Realtime Block List will reject 70% to 90% of inbound emails. If you are receiving a high volume of spam email, the likelihood is that you Realtime Block List is not updating as it should and you should seek technical advice.
Book Free Demo
Did You Know?
99.99%
SpamTitan's spam catch rate
11 Seconds
a ransomware attack occurs
$285
the average cost to manage spam per person without an email filter
56.50%
of all email is spam
2. Engage SMTP Handshake Protocols
SMTP controls perform a variety of functions and first-line tests. The most important is the “SMTP handshake” in which your inbound mail server will look for a HELO command, a Fully Qualified Hostname or a Resolvable Hostname. By engaging SMPT handshake protocols, your email filter will reject any email originating from an address with no DNS A or MX record.
The process for engaging SMTP handshake protocols requires a small adjustment to your email server or spam filter, but it may be necessary for you to create a whitelist of approved senders for suppliers or customers with incorrectly configured email servers to allow their emails to be accepted. Unfortunately, this is one of our anti-spam tips not suitable for Managed Service Providers.
3. Activate Recipient Verification Inspection
Recipient Verification Inspection checks that each inbound email is addressed to a valid recipient. Spammers often use addresses such as “info@” or “admin@” to get their emails opened by an unsuspecting end-user - potentially loading malware onto your network or generating a response from the end-user that leads to a breach of confidential information.
Recipient Verification Inspection can be activated by uploading your valid email addresses to your mail server or spam filter. Like the two tips for reducing spam emails given above, Recipient Verification Inspection rejects spam email before it is downloaded, reducing the load on your email server and saving bandwidth. Make half an hour this week to implement these three, and you will probably save yourself weeks of work over the next year.
Book Free Demo
4. Block (or at least Quarantine) Potentially Dangerous Attachment Types
Most computer users are aware of the risks of downloading .exe files, so spammers rarely send malware via an attachment with an .exe extension. Instead they hide the payload file within an image, spreadsheet, document or PDF file, or change the extension name to circumnavigate filtering mechanisms.
It is impractical to block every possible type of attachment that could be harboring malware but, with MIME filtering software, you can block the attachments most frequently associated with malicious code (.exe, .bat, .scr, etc.) and quarantine others that would normally be sent and received via secure file sharing facilities such as Dropbox and Google Drive.
5. Scan Inbound and Outbound Mail for Viruses
Undoubtedly every individual and organization will have some form of antivirus software already protecting their network. However proprietary antivirus software typically works retrospectively - identifying malware once it has been downloaded. Consequently it is recommended that you implement secondary antivirus software to scan inbound and outbound mail.
The importance of scanning outbound mail (for spam as well as for viruses) is that some system administrators set their spam filters parameters to “over-zealous”. If emails originating from your IP address are too frequently identified as being infected (or containing spam), you could find the IP address added to a Realtime Block List and all your outbound emails rejected by their recipients.
6. Scan Inbound Mail for Malicious URLs
As well as harboring viruses, inbound email can contain links to exploited websites and websites built to conduct phishing campaigns. Therefore, one of our anti-spam tips relating to mitigating risks from web-borne threats is that, whatever inbound mail antivirus software you deploy, make sure it has malicious URL blocking and phishing protection (tip: not all antivirus software performs these functions).
Malicious URL blocking and phishing protection uses “URIBL” and “SURBL” protocols to compare links contained within emails against a global blacklist of domain names frequently found in unsolicited bulk email and known phishing sites. These mechanisms reject any email containing a malicious URL or link to a phishing website to protect your organization from fraud and theft.
Book Free Demo
7. Ensure Your Spam Filter Uses Bayesian Analysis
Bayesian Analysis is a mechanism based on a spam pattern library that identifies trends in spam emails. A spam pattern library contains a large database of recent and historical spam provided by the spam-fighting community, and Bayesian Analysis uses this data - along with potentially dangerous attachment types and identified malicious URLs - to reject emails falling beneath an acceptance threshold.
Rather than being a static mechanism, Bayesian Analysis “learns” to recognize new spamming techniques and “forgets” old spam patterns than may now block legitimate emails. The analysis can be improved if you correct false positives (genuine emails rejected/blocked in error) as they occur, and instruct your end-users to tag any spam that gets through your filter.
8. Set an Appropriate Acceptance Threshold
It was mentioned above that some system administrators set their spam filters parameters to “over-zealous”. Although this may be a slight exaggeration, different organizations will have different spam acceptance thresholds depending on the nature of their business. Spam filters assign a score to each inbound email based on its content, and it is up to system administrators to determine an appropriate score.
Finding the optimum level of filtering to reduce spam and false positives to a minimum level can take a little trial and error. Most vendors of spam filtering solutions and service providers allow organizations a trial period to evaluate the solution/service. You should use this time to find an appropriate acceptance threshold and fine-tune as necessary as you become more familiar with the filter.
9. Make Use of Group Settings where Available
Some - but not all - spam filters have the flexibility to set spam acceptance thresholds by individual user, user-group or universally. In some circumstances it may be necessary for system administrators to apply different settings for different user-groups in order to maximize the effectiveness of the anti-spam filtering solution.
A scenario in which this feature may be necessary is when a business´s sales team receive leads by email. Like all sales leads, these leads need to be acted upon quickly, so it is important they are not quarantined as spam and it may be necessary to apply a lower spam acceptance threshold for the sales department than - for example - the finance department.
Book Free Demo
10. Block New Sources of Spam with Greylisting
We have saved one of the most important tips for reducing spam emails until the end - Greylisting. Most of the mechanisms listed in our anti-spam tips rely on identifying “known” sources of spam to reject inbound emails. However, spammers are constantly trying to circumnavigate filtering mechanisms by using new or “unknown” sources from which to send spam.
Greylisting works by requesting that the sender´s server resends the email. Typically, spammers´ servers are too busy sending out spam emails to respond to the request and, after a period of time without receiving the resent email, the Greylisting function rejects the email as spam. Greylisting can be the difference between your spam filter identifying 96% of spam or virtually 100% of spam. SpamTitan will block 99.97% of spam email.
11. User Sandboxing for Advanced Protection
SpamTitan sandboxing protects against breaches and data loss from zero-day threats and advanced email attacks. Sandboxing provides a safe environment to run in-depth, sophisticated analysis of suspicious programs and files. SpamTitan sandboxing protects against malware, phishing, advanced persistent threats (APTs) and malicious URLs. This feature also offers indepths insight into new threats and helps mitigate risks.
Hear from our customers
Summary of Top Ten Anti-Spam Tips
- Make sure your filter´s Realtime Block List updates in real time.
- Configure your filter to engage SMTP handshake protocols.
- Upload valid email addresses to facilitate recipient verification inspection.
- Block potentially dangerous attachments by file extension.
- Scan inbound and outbound mail for virus and malware.
- Scan inbound mail for malicious URLs using URIBL/SURBL filters.
- Ensure Bayesian Analysis is activated so your filter can “learn” as it filters.
- Take advantage of free trials to find spam acceptance thresholds.
- Where possible, apply spam acceptance thresholds by user or group.
- Activate the Greylisting process whenever the option exists on your filter.
- Take advantage of the sandboxing feature for advanced protection
Education is One of the Best Anti-Spam Tips
Although unrelated to the functions of a spam filter, some of the best spam email advice is to educate your end-users about the threat from spam email. System administrators are often divided on whether they should act as a protector for their end-users or rely on end-users´ common sense. Unfortunately, the former is the safest option. Train your users to prevent infections. It only takes one click on a malicious link or the disclosure of an end-user´s login credentials for your organization to potentially face financial ruin.
Implementing an email usage policy that includes best practices for identifying, tagging and reporting spam, malware, viruses and phishing attempts could substantially reduce the amount of spam your organization receives and its potential impact. It is also advisable to test your end-user´s compliance with the email usage policy by sending them “fake” phishing emails to see how they are dealt with. Phishing email simulations will greatly improve security awareness of the workforce. When a simulation email is failed it can be turned into a training opportunity. Over time, susceptibility to phishing emails can be greatly reduced through training and phishing simulations.
Spam Filtering Solutions from SpamTitan
SpamTitan has been developing spam filtering solutions since 1999. Over 8,500 businesses and 2,500 MSPs use our solutions due to their ease-of-use and high level of spam email detection (99.97% according to leading independent online testing and certification authority - VB Bulletin). We protect your customers from malware, ransomware, phishing, viruses, botnets and other cyber threats.
Our two spam filtering solutions - SpamTitan Cloud and SpamTitan Gateway - both have the mechanisms and versatility highlighted in our anti-spam tips to reduce spam. Each of the mechanisms can be adjusted easily through our web-based portal to fine-tune the filters to your exact requirements.
SpamTitan Cloud and SpamTitan Gateway also help your organization mitigate risks from email-borne threats with dual antivirus software provided by Bitdefender and ClamAV. The high level of antivirus protection includes malicious URL blocking and phishing protection.
Our spam filtering solutions are backed by industry-leading customer and technical support. In the unlikely event that you encounter a problem with either of our products, our teams are on standby to resolve any issues you may have.
Try SpamTitan´s Spam Filtering Solutions for Free
The best way for an organization to evaluate a spam filtering solution and apply our anti-spam tips is to test the abilities of the solution in their own environment. Consequently we are offering all organizations a free fourteen day trial of SpamTitan Cloud or SpamTitan Gateway with no obligation to continue with the service once the trial period is over.
Our offer consists of a fully-enabled, enterprise grade spam filtering service for fourteen days with full customer and technical support, plus help with applying our anti-spam tips wherever possible. To find out more about our offer, speak with our customer service team today. Our team will be happy to answer any questions you have, and guide you through the quick and easy process of installing and configuring the most appropriate SpamTitan spam filtering solution for your organization´s needs.
SpamTitan is a multi-award-winning email protection, spam filtering, and email filtering solution. Start your free trial for SpamTitan today to discover how we can prevent malware attacks.
Related Articles
Frequently Asked Questions (FAQs)
How do spam filters identify zero-day malware threats?
AV engines are used to detect known malware threats, but zero-day malware will not be detected. To detect those new malware threats, sandboxing is required. Email attachments are sent to the sandbox where they are subjected to in-depth analysis to identify any malicious actions such as C2 callbacks.
Does greylisting delay the delivery of emails?
Greylisting is important for detecting new sources of spam, but there will be a small delay in receiving emails as a result. To ensure business-critical emails are not delayed, most businesses use whitelisting. Whitelisting ensures all emails from a trusted source will not be subjected to the greylisting process and will be delivered immediately.
Why is outbound email filtering important?
Outbound email filtering allows organizations to identify potential email account compromises and prevent corporate email accounts for being used for spamming, phishing, and distributing malware. Outbound filtering protects IP reputation and allows breaches to be identified quickly. Outbound scanning is also important for data leak prevention. Data can be tagged and prevented from being emailed externally and restrictions can be placed on the file types that can be emailed externally.
How much does an advanced spam filtering solution cost?
An advanced spam filtering solution should pay for itself in terms of the threats the solution blocks and the improvements to productivity by blocking spam and malicious emails. You might be surprised to hear an advanced, feature-rich solution such as SpamTitan is only likely to cost you around $1 per user per month, and even less if you take advantage of the discounts available for multi-year contracts.
Can SpamTitan improve spam detection on Office 365?
Office 365 provides a reasonable level of spam protection, but reasonable is not good enough for many businesses. SpamTitan has been developed to integrate seamlessly with Office 365 and augment the anti-spam and threat protection features of Office 365 to provide far greater protection against spam, phishing, spear phishing, malware, ransomware, and other email threats.


