There has been an increase in malspam campaigns spreading Emotet malware in recent weeks, with several new campaigns launched that spoof financial institutions – the modus operandi of the threat group behind the campaigns.
The Emotet malware campaigns use Word documents containing malicious macros. If macros are enabled, the Emotet malware payload is downloaded. The Word documents are either sent as email attachments or the spam emails contain hyperlinks which direct users to a website where the Word document is downloaded.
Various social engineering tricks have been used in these campaigns. One new tactic that was identified by Cofense is the wrapping of malicious hyperlinks in Proofpoint’s (PFPT) TAP URL Defense wrapping service to make the email appear benign.
According to Cofense, the campaign delivers Emotet malware, although Emotet in turn downloads a secondary payload. In past campaigns, Emotet has been delivered along with ransomware. First, Emotet steals credentials, then the ransomware is used to extort money from victims. In the latest campaign, the secondary malware is the banking Trojan named IcedID.
A further campaign has been detected that uses Thanksgiving themed spam emails. The messages appear to be Thanksgiving greetings for employees, and similarly contain a malicious hyperlink or document. The messages claim the document is a Thanksgiving card or greeting. Many of the emails have been personalized to aid the deception and include the user’s name. In this campaign, while the document downloaded appears to be a Word file, it is actually an XML file.
Emotet malware has been updated recently. In addition to stealing credentials, a new module has been added that harvests emails from an infected user. The previous 6 months’ emails – which include subjects, senders, and message content – are stolen. This new module is believed to have been added to improve the effectiveness of future phishing campaigns, for corporate espionage, and data theft.
The recent increase in Emotet malware campaigns, and the highly varied tactics used by the threat actors behind these campaigns, highlight the importance of adopting a defense in depth strategy to block phishing emails. Organizations should not rely on one cybersecurity solution to provide protection against email attacks.
Phishing campaigns target a weak link in security defenses: Employees. It is therefore important to ensure that all employees with corporate email accounts are taught how to recognize phishing threats. Training needs to be ongoing and should cover the latest tactics used by cybercriminals to spread malware and steal credentials. Employees are the last line of defense. Through security awareness training, the defensive line can be significantly strengthened.
As a frontline defense, all businesses and organizations should deploy an advanced spam filtering solution. While Office 365 email includes a basic level of protection against phishing attacks, a powerful third-party anti-phishing and spam filtering solution is required to provide protection against more sophisticated email attacks.
SpamTitan is an advanced email filtering solution that uses predictive techniques to provide superior protection against phishing attacks, zero-day attacks, and new malware variants that bypass signature-based defenses.
In addition to scanning message content, headers, attachments, and hyperlinks for spam and malware signatures, SpamTitan uses heuristics, machine learning, and Bayesian analysis to identify emerging threats. Greylisting is used to identify and block large scale spam campaigns, such as those typically conducted by the threat actors spreading banking Trojans and Emotet malware.
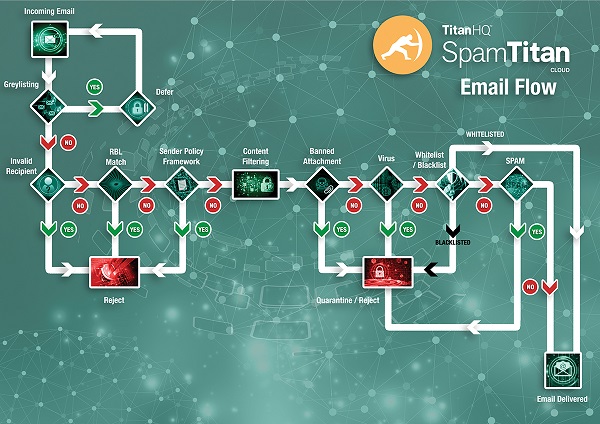
How SpamTitan Protects Businesses from Email Threats
A web filter – such as WebTitan – adds an additional layer of protection against web-based attacks by preventing end users from visiting malicious websites where malware is downloaded. A web filter assesses all attempts to access web content, checks sites against blacklists, assesses the domain, scans web content, and blocks access to sites that violate its policies.
For further information on how you can improve your defenses against web-based and email-based attacks and block malware, ransomware, botnets, viruses, phishing, and spear phishing attacks, contact TitanHQ today.
