What is Network Segmentation?
Network segmentation is the act of dividing a computer network into smaller physical or logical components. Two devices on the same network segment can then talk directly to each other. For communication to happen between segments, the traffic must flow through a router or firewall. This passage allows for traffic to be inspected and security policies to be applied.
Network segmentation is one of the mitigation strategies in terms of protecting against data breaches and multiple types of cyber security threats. In a segmented network, device groups have the connectivity required for legitimate business use only. The ability of ransomware to spread is greatly restricted. However all too often organizations operate an unsegmented network.
Network segmentation can also help to boost performance. With fewer hosts on each subnet, local traffic is minimized. It can also improve monitoring capabilities and helps IT teams identify suspicious behavior.
If you follow network segmentation best practices and set up firewall security zones you can improve security and keep your internal network isolated and protected from web-based attacks.
Book Free Demo
Network Segmentation Benefits
There are many benefits to be gained from network segmentation, of which security is one of the most important. Having a totally flat and open network is a major risk. Network segmentation improves security by limiting access to resources to specific groups of individuals within the organization and makes unauthorized access more difficult. In the event of a system compromise, an attacker or unauthorized individual would only have access to resources on the same subnet. If access to certain databases in the data center must be given to a third party, by segmenting the network you can easily limit the resources that can be accessed, it also provides greater security against internal threats.
Network Segmentation Best Practices
Most businesses have a well-defined network structure that includes a secure internal network zone and an external untrusted network zone, often with intermediate security zones. Security zones are groups of servers and systems that have similar security requirements and consists of a Layer3 network subnet to which several hosts connect.
The firewall offers protection by controlling traffic to and from those hosts and security zones, whether at the IP, port, or application level. There are many network segmentation examples, but there is no single configuration that will be suitable for all businesses and all networks, since each business will have its own requirements and functionalities. However, there are network segmentation best practices that should be followed. We have outlined these and firewall DMZ best practices below.
Suggested Firewall Security Zone Segmentation
Suggested Firewall Security Zone Segmentation
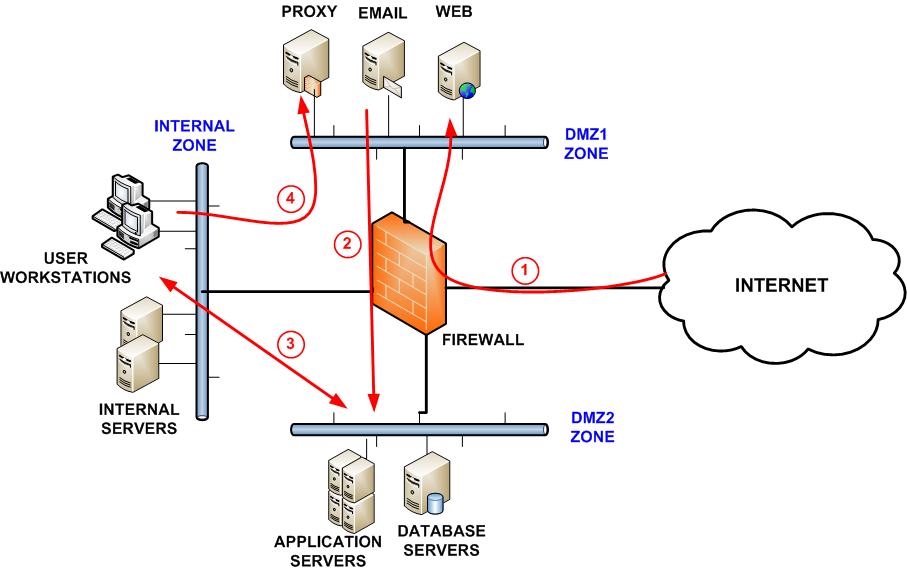
In the above illustration we have used firewall security zone segmentation to keep servers separated. In our example we have used a single firewall and two DMZ (demilitarized) zones and an internal zone. A DMZ zone is an isolated Layer3 subnet.
The servers in these DMZ zones may need to be Internet facing in order to function. For example, web servers and email servers need to be Internet facing. Because they face the internet, these servers are the most vulnerable to attack so should be separated from servers that do not need direct Internet access. By keeping these servers in separate zones, you can minimize the damage if one of your Internet facing servers is compromised.
In the diagram above, the allowed direction of traffic is indicated with the red arrows. As you can see, bidirectional traffic is permitted between the internal zone and DMZ2 which includes the application/database servers, but only one-way traffic is permitted between the internal zone and DMZ1, which is used for the proxy, email, and web servers. The proxy, email, and web servers have been placed in a separate DMZ to the application and database servers for maximum protection.
Traffic from the Internet is allowed by the firewall to DMZ1. The firewall should only permit traffic via certain ports (80,443, 25 etc.). All other TCP/UDP ports should be closed. Traffic from the Internet to the servers in DMZ2 is not permitted, at least not directly.
A web server may need to access a database server, and while it may seem a good idea to have both of these virtual servers running on the same machine, from a security perspective this should be avoided. Ideally, both should be separated and placed in different DMZs. The same applies to front end web servers and web application servers which should similarly be placed in different DMZs. Traffic between DMZ1 and DMZ2 will no doubt be necessary, but it should only be permitted on certain ports. DMZ2 can connect to the internal zone for certain special cases such as backups or authentication via active directory.
The internal zone consists of workstations and internal servers, internal databases that do not need to be web facing, active directory servers, and internal applications. We suggest Internet access for users on the internal network to be directed through an HTTP proxy server located in DMZ 1.
Note that the internal zone is isolated from the Internet. Direct traffic from the internet to the internal zone should not be permitted.
The above configuration provides important protection to your internal networks. In the event that a server in DMZ1 is compromised, your internal network will remain protected since traffic between the internal zone and DMZ1 is only permitted in one direction.
Book Free Demo
Risks of an Unsegmented Network
A real world example of an unsegmented network and resulting attack is the massive Target data breach of 2013. Reportedly, the Target breach had its origin in a phishing email opened by an employee at a small HVAC company that did business with Target. The malware lurked in the HVAC network for two months before moving on to attack the Target network.
Once inside they were able to move laterally through Target’s internal network, eventually installing malware on point-of-sale (POS) terminals throughout the stores. In the wake of the attack, Target implemented network segmentation to prevent the lateral movement that allows the attackers move with the system in this breach.
It’s no surprise a breach this huge is massively expensive and the cleanup represents an almost overwhelming challenge. Bloomberg BusinessWeek reported that Target spent $61 million through Feb. 1 on the breach.
The damage?
- The data of 110 million customers was compromised.
- Over 100 lawsuits have been filed.
- Banks have already spent $200 million related to the Target breach, and it’s unclear if there’s an even bigger payout on the horizon.
Effective network segmentation also makes it easier to detect signs of an attack. It’s not uncommon for a company’s Intrusion Detection System to generate such a large number of alerts that many go uninvestigated.
By concentrating on alerts related to sensitive parts of the network, security teams can prioritize incidents likely to be the most dangerous. Network segment traffic can also be monitored for unusual patterns or activity potentially indicating an attack.
Effective Network Segmentation is not enough
Many sectors including manufacturing, retail and industrial are prime target for cyberattacks. Often organizations in these sectors are not up to date in terms of implementing key cybersecurity controls in order to be prepared for advanced and evolving attack methods.
By adhering to network segmentation best practices, you can optimize network security. There's no silver bullet to take down every attacker, but it’s possible to implement several layers of security that work together as a whole to defend against a myriad of attacks.
Book Free Demo
Layered Security to Prevent Data Breaches
Layered security allows for each security layer to compound with the others to form a fully functioning, complete sphere of security. The internal network (ideally segmented) and its data are surrounded by powerful, interwoven layers that an attacker must defeat. These layers make security much more complex for a successful breach.
Cybercriminals are already exploiting the lack of security at the DNS layer to conduct phishing attacks and gain access to proprietary enterprise data. Not securing the DNS layer is making it far too easy for hackers to take advantage. Securing the DNS layer is a straightforward process that requires no additional computer hardware or even any software installations. Many vendors now offer cloud based DNS filtering solutions that can be set up in minutes.
Isn’t it about time you started securing the DNS layer and making it much harder for cybercriminals to compromise your network? If you’re looking to get enterprise-grade protection from malware and phishing, check out >WebTitan Cloud DNS filtering today.
FAQs
What does network segmentation mean?
Network segmentation is concerned with dividing a network up into smaller segments called subnets. This can improve network performance and is important for security. By using firewalls between each segment, you can carefully control access to applications, devices, and databases and can block lateral movement in the event of a successful cyberattack.
What is logical network segmentation?
Logical network segmentation is a popular way of segmenting a network. Instead of segmenting physical parts of the network such as routers and access points, logical segmentation uses concepts built into network infrastructure for segmentation, such as creating virtual local area networks (VLANS) that may share physical hardware.
Is network segmentation necessary for PCI compliance?
Organizations that store, process, and/or transmit cardholder data must comply with PCI DSS. One of the requirements is to use network segmentation to keep the cardholder data environment (CDE) separate from other parts of the network. Through network segmentation, organizations can isolate credit card data from all other computing processes.
Can network segmentation protect against ransomware attacks?
Network segmentation is a best practice that can help to reduce the damage caused by a malware or ransomware attack. If a computer is compromised, attackers will attempt to more laterally and access other devices and parts of the network. With network segmentation, lateral movement is much harder, so it is easy to contain malware and limit file encryption by ransomware.
What are the main benefits of network segmentation?
There are three main benefits of network segmentation. First is security. It reduces your attack surface and limits lateral movement in the event of a breach. Second, you can improve network performance, as traffic will be confined to the part of the network where it is required. Thirdly, it makes compliance easier by allowing you to separate regulated data from other computer systems.