Cybersecurity News
Keeping up-to-date with cybersecurity news can help protect organizations from online threats such as malware downloads and phishing campaigns. By being aware of type of threats that exist, how they operate, and what damage they can do, organizations can take precautions against the threats, educate their employees to be aware of online security, and strengthen their online defenses.
The most effective way of preventing attacks by cybercriminals is to stop Internet users from receiving emails containing phishing links or visiting websites that harbor viruses. This can be achieved with an email filter and an Internet content filter – both solutions having mechanisms in place to protect organizations and ensure they are not featured in future in our cybersecurity news section.
Apr 29, 2016 | Cybersecurity News
One cybercriminal gang has resorted to a mafia-style protection racket to obtain money, although it would appear that businesses are being sent empty DDoS threats. While many companies have sent money to the criminal gang, which claims to be the Armada Collective, there is no evidence to suggest that the gang is following through on its threat of conducting a largescale Distributed Denial of Service attacks.
Empty DDoS Threats Still Proving Lucrative for Attackers
The gang has been sending emails to businesses threatening them with a powerful DDoS attack if they do not send protection money to the gang. The demands appear to range from 10 to 50 Bitcoin and over 100 organizations have given in to the attackers demands according to DDoS mitigation vendor CloudFlare. So far the gang has gathered around $100,000 in payments, yet no DDoS attacks have been conducted.
Armada Collective is the name of a hacking group already known to conduct massive DDoS attacks. The emails claim that the gang is able to deliver a DDoS attack in excess of 1 Tbps per second. The group also claims to be able to bypass security controls set up to protect against DDoS attacks. In case recipients of the email are in any doubt as to who the attackers are and what they are capable of, they are advised to conduct a search on Google. Armada Collective has been known to conduct DDoS attacks up to 500 Gbps.
Are the Latest Emails from a Copycat Group?
According to CloudFlare, it may not be a case of the hackers not having the capability to pull off a large scale DDoS attack on companies that do not pay, rather the attackers may not be able to tell who has paid and who has not. The emails are reusing Bitcoin addresses so there is no way of confirming which companies have paid. Emails are also being sent containing the same text and payment demands, regardless of the size of the organization.
However, the empty DDoS threats or not, many companies are unprepared to take the risk and have paid between $4,500 and $23,000 to stop the attacks.
CloudFlare suspects that the extortionists are not who they claim to be. The Armada Collective has not been conducting attacks for some time. CloudFlare researchers believe that the group has been operating under a different name – DD4BC. However, suspected members of that group have been arrested as part of Operation Pleiades last year – an International effort to bring down hacking groups that have been conducting DDoS attacks.
The group behind this campaign may well be imposters, although many hackers send out threats of DDoS attacks along with demands for payment. Some of those attackers are more than willing to follow through on the threats and have the capability to launch attacks.
It is never a good idea to give into attackers’ demands, but it is important to ensure that protections have been put in place to resist DDoS attacks and to seek advice before taking any action if an email demand is received.
Apr 22, 2016 | Cybersecurity Advice, Cybersecurity News, Web Filtering
The healthcare industry has had a hard time in recent months; however, it is far from the only industry being targeted by hackers. Manufacturing company cyberattacks are on the increase and the industry is now second only to healthcare according to a new report from IBM X-Force Research. The manufacturing industry has replaced the financial sector as hackers attempt to gain access to intellectual property. Intellectual property can be sold for big bucks on the black market.
$400 Billion Worth of Intellectual Property Is Stolen from U.S. Companies Every Year
According to figures from the Federal Bureau of Investigation, each year over $400 billion worth of intellectual property is stolen from the United States and sold overseas. Many of the attacks are conducted by nation-state backed hacking groups, although a number of players have now got in on the act due to the value of data and the relative ease of breaking through manufacturing company cybersecurity defenses.
According to the IBM’s 2016 Cyber Security Intelligence Index, manufacturers in the automotive sector were most frequently targeted. Chemical companies were the second most likely to be attacked. 30% of manufacturing company cyberattacks took place on automotive manufacturers.
Not only are the potential rewards for successful manufacturing company cyberattacks high, attacks are relatively easy to pull off. A successful attack on a company in the financial sector may be rewarding, but the defenses put in place to keep hackers at bay are usually far more robust than in less well regulated industries such as manufacturing. The manufacturing industry has been relatively slow to improve cybersecurity defenses.
Organizations in the healthcare industry are required to comply with the Health Insurance Portability and Accountability Act or HIPAA for short. HIPAA sets a number of minimum standards which must be met by all healthcare organizations. Administrative, technical, and physical safeguards must be implemented to keep patient data protected. The legislation has forced healthcare companies to improve their cybersecurity defenses.
Similarly, legislation has been introduced that requires organizations in the financial services industry to improve protections to keep data secure. Organizations must comply with the Gramm-Leach-Bliley Act and implement Payment Card Industry Data Security Standards. With no equivalent legislation covering the manufacturing industry, companies have not been forced to improve their cybersecurity defenses. While many organizations have implemented robust multi-layered security defenses, data security standards are higher in the healthcare and financial services verticals.
Many Manufacturing Company Cyberattacks Target Employees
With the number of manufacturing company cyberattacks increasing, cybersecurity defenses need to be improved. Many of the attacks target end users. Phishing and spear phishing emails can be a highly effective way of getting past security defenses. Employees are seen to be the weakest link in the security chain.
IBM X-Force senior threat researcher John Kuhn pointed out that servers are being targeted by hackers using phishing and spear phishing schemes. If employees can be lured onto malicious websites, vulnerabilities can be exploited and malware downloaded onto computers. From there it is a small hop to network servers.
Providing security training to staff is essential to reduce the risk of phishing attacks being successful. However, training alone is not sufficient to prevent all attacks. Software solutions should also be used to make it harder for end users to inadvertently install malware. A web filter should be implemented to prevent end users from downloading malicious software and visiting compromised websites. Web filtering can be a highly effective way of preventing attacks that target employees.
It is also essential to conduct comprehensive risk assessments to identify security vulnerabilities. All systems need to be assessed regularly. Any vulnerabilities identified need to be promptly addressed.
Apr 14, 2016 | Cybersecurity News
A recent investigation by cyber security company F-Secure has revealed that corporate network cybersecurity defenses are anything but secure. The company recently assessed the cybersecurity protections in place at a large number of companies and discovered thousands of security vulnerabilities that could all too easily be exploited by hackers.
Holes in Corporate Network Cybersecurity Defenses Could be Easily Plugged
The company discovered almost 85,000 vulnerabilities in corporate network cybersecurity defenses. 7% of the 100 most common flaws were severe according to National Vulnerability Database standards, and half of those vulnerabilities could be exploited remotely by hackers. In the majority of cases patches were available to address the vulnerabilities yet they had not yet been installed.
Numerous system misconfigurations were also discovered which could potentially be exploited by attackers. Simple administrative changes could address many of the vulnerabilities discovered by the researchers.
The top ten vulnerabilities discovered by F-Secure had a severity rating of low to moderate. While these vulnerabilities may not allow hackers to gain access to corporate networks, they indicate that the organizations in question do not have strong cybersecurity defenses. If these vulnerabilities were to be discovered by hackers, it could result in the company being probed and tested. In some cases, closer inspection would reveal exploitable weaknesses.
Previous research conducted by the United States Computer Emergency Readiness Team (US-CERT) suggests that in 85% of cases, targeted cyberattacks can be prevented by applying patches. However, F-Secure’s research indicates that patch management practices are substandard in many organizations. Even when patches are applied, all too often they are not applied to all systems and vulnerabilities are allowed to remain.
If patches are not applied to all systems and vulnerabilities are allowed to persist, it is only a matter of time before corporate network cybersecurity defenses are breached.
Internet Threats Now Reaching Critical Levels
An Internet security threat report issued by Symantec earlier this month shows that the threat to corporate networks is greater than ever before. Web-borne threats have increased substantially, while three quarters of websites were determined to contain vulnerabilities that could potentially be exploited by hackers.
Furthermore, the number of zero-day vulnerabilities doubled in 2015. As soon as a vulnerability is uncovered it is rapidly incorporated into exploit kits. Those exploit kits probe for these vulnerabilities and use them to download malware and ransomware.
The threat report also confirmed that ransomware attacks increased by 35% in 2015, while spear phishing attacks increased by 55%. Attacks on large organizations are to be expected, but the report showed that even small businesses are being attacked with increasing regularity.
Unless organizations make it harder for hackers to break through their defenses, the rise in successful cyberattacks is likely to continue.
Have you recently performed a complete risk assessment to check for security vulnerabilities?
Are you certain that all security holes in your company’s defenses have been plugged?
Apr 8, 2016 | Cybersecurity Advice, Cybersecurity News, Internet Security News
The dramatic rise in business email scams in the past 12 months has prompted the Federal Bureau of Investigation (FBI) to issue a new warning. Companies of all sizes are being targeted with business email compromise scams which relieve companies of tens of thousands if not hundreds of thousands or millions of dollars.
The FBI warns that scammers are now going to extraordinary lengths to fool company employees into making transfers of large sums of company funds into hacker’s accounts. These attacks are far from the random email spam campaigns typically associated with email scammers. Companies are extensively researched, individual targets are identified, and carefully crafted emails are sent. A variety of social engineering techniques are employed to convince an individual in the company to make a sizeable bank transfer to the attacker’s account.
There are two main variants of these business email scams. The first involves gaining access to the email account of the CEO or a senior executive in the company. This is usually achieved with a spear phishing campaign. This phase of the attack involves researching the company and identifying a target. That target is then sent a spear phishing email in order to gain access to their email login credentials.
Once access to an email account has been gained, emails are checked to determine the style of writing used by that individual – How they sign their emails, the terminology they use, and the level of familiarity they have with the second target: An individual that manages money or makes bank transfers for the company.
An email is then sent from the executive’s email account requesting a transfer be made. Account details are supplied with a reason for urgency, and an explanation of why the request is being made.
Since the emails come from a known source within the company, and the terminology and style of the email matches those typically received by the accounts department, the transfer is often made without being queried.
Another variation on the same theme does not require access to an email account. Instead a domain name is purchased that is virtually identical to that used by the target company, often with just two letters transposed. Typically, an L in the domain name is replaced with the numeral 1, or the letter O with a zero. Goog1e.com instead of google.com for example.
These business email scams are highly effective because they take advantage of employees’ reluctance to query requests from authority figures in their organization. The emails are also crafted so as not to arouse suspicion.
Business Email Scams Have Netted Criminals Over $2.3 Billion in Three Years
Over the past three years the FBI has received complaints about business email scams from over 79 countries, and from every state in the U.S. Recently attacks have spiked in Phoenix, with other U.S. cities also targeted. Between October 2013 and February 2016, the FBI has been informed of 17,642 victims of these attacks. Over $2.3 billion in losses have been reported.
However, recently the situation has become dire. There has been a 270% increase in business email scams since January 2015, and the amounts lost in each successful attack are substantial. FBI reports that in Arizona the typical transfers requested are between £$25,000 and $75,000. With such high rewards for criminals it is no surprise that so many attacks are being conducted.
The FBI has urged companies to exercise caution and to be on high alert for these business email scams. The advice provided is to be extremely wary of any email-only request for a wire transfer, even if it comes from within the company.
To prevent these attacks, accounts department staff should verify a transfer request with the individual by phone – never by email – and should check the email address of the sender carefully. Multi-level authentication of bank transfers should also be consider3ed to reduce the risk of a successful attack.
Apr 5, 2016 | Cybersecurity News, Network Security
2015 may have been the year of the healthcare data breach, but 2016 is fast becoming the year of ransomware with new strains such as Samas ransomware appearing at an alarming rate. Recently the Federal Bureau of Investigation reached out to U.S. businesses, seeking help to deal with the latest Samas ransomware threat.
Samas Ransomware Being Used to Encrypt Networks
Samas ransomware – also known as Samsa, Samsam, and MSIL – is different from many strains of ransomware that were used by cybercriminals last year. The new ransomware strain is being used to attack businesses rather than consumers. Last year, criminals were sending out ransomware randomly via spam email.
Ransom demands of 0.5-1 Bitcoin were the norm, with consumers often willing to pay to recover their files, accounts, photographs, and other important data. However, businesses hold far more valuable data. If criminals are able to infect enterprise computers and encrypt important business files, higher ransom demands can be sent. In many cases those demands have been paid.
In order to obtain large ransoms, cybercriminals need to infect networks rather than single computers. If an end user downloads ransomware onto their computer, and that ransomware has the capability to spread laterally and infect other systems, enterprises are more likely to pay to unlock the encryption. Even when viable backups exist, the complexity of some of the ransomware now being used makes paying the ransom an easier and lower cost option. Since some ransomware is capable of deleting backup files, the restoration of data may simply not be an option. Samas ransomware has been reported to delete Volume Shadow Copy Service (VSS) data.
Access to Systems is Gained by Cybercriminals Weeks Before Samas Ransomware is Deployed
The mode of action of Samas ransomware is different from other families of malicious file-encrypting software such as Locky, CryptoWall, and Cryptolocker.
Attackers are exploiting a vulnerability in the JBoss enterprise application platform to compromise an external web server. This is achieved by using a security program called JexBoss. Once access to a server has been gained, attackers mask communications using a Python based SOCKS proxy. A variety of software tools are then used to gain access to login credentials, and they in turn are used to compromise other systems and devices within an organization’s infrastructure. Several different tactics are then used to deploy Samas ransomware on numerous machines.
Several analyses of infected systems were conducted by Dell SecureWorks, which revealed attackers had compromised systems several weeks or months before the ransomware was actually deployed. Had the system compromise been detected earlier, the ransomware infections could have been avoided. Unfortunately, the initial compromise is difficult to detect, and anti-virus products are slow to detect new threats such as Samas ransomware.
Apr 1, 2016 | Cybersecurity News, Network Security, Web Filtering
The FBI issued warnings last year over the rise in popularity of Bitcoin ransomware, and a few days ago the law enforcement agency reached out to companies requesting assistance to help it tackle the threat from the latest ransomware variants, just days before the malicious software was used on MedStar Health System.
Over the last few weeks a number of healthcare institutions have reported being attacked with ransomware, and there is no telling how many companies have had corporate and customer data encrypted by attackers. Many do not like to advertise the fact they have been attacked.
While attacks on individuals only result in relatively small ransoms being paid, the same cannot be said for companies. Ransom demands of tens of thousands of dollars are issued, and many companies feel they have little alternative but to pay the ransom demand in order to recover their data.
Unfortunately for enterprises, the threat from Bitcoin ransomware is unlikely to go away any time soon. More cybercriminals are getting in on the act and attacks will continue as long as they prove to be profitable. The bad news is Bitcoin ransomware is very effective. Worse still, attacks require little technical skill and cost very little to pull off.
Bitcoin Ransomware Kits Mean Little Skill is Required to Pull Off a Successful Attack
According to a report in the Italian newspaper La Stampa, the cost of conducting a ransomware attack can be shockingly low and requires little in the way of skill. One reporter at the newspaper set out to discover just how easy it is to buy ransomware and conduct an attack. After visiting underground forums on the darknet, the researcher found a board where ransomware-as-a-service was being offered.
One poster on a Russian forum was not only offering ransomware for sale, but made it exceptionally easy for would-be cybercriminals to conduct campaigns. The purchaser would be supplied with the ransomware, distribution tools to send out the malicious file-encrypting software via email and advertising networks, and this Bitcoin ransomware service could be bought for as little as $100.
According to the article, the purchaser would be allowed to keep 85% of the ransoms that were collected, with the remaining 15% going to the seller of the service. There appears to be no shortage of takers. The hacker behind this campaign allegedly has between 300 and 400 active customers. This is only one seller. There are many more offering such a service. The campaigns may not be particularly sophisticated, but the reality is that they don’t actually need to be.
Some sellers even offer Bitcoin ransomware kits where purchasers only need to enter in their Bitcoin address for the payment of the ransom, the amount they wish to charge their victims for the security keys, and they can download everything they need, including instructions on how to run the campaign. These services are not being sold for big bucks. The sellers know they can earn considerable sums by taking a cut of the ransoms that are paid.
The standard rates being charged by attackers to supply security keys for single computer infections is between 0.5 and 1 Bitcoin – approximately $200-$425. All that is required for an attacker to make a profit is one or two victims to install the Bitcoin ransomware and pay for a security key. According to data released by Tripwire, half of American ransomware victims have ended up paying the ransom demand to recover their data.
Until law enforcement efforts to track down attackers and shut down underground forums improve, and victims stop paying ransoms, the attacks are likely to continue to increase.
What businesses need to do is to make sure they are better protected to prevent Bitcoin ransomware from being installed and to ensure they have viable backups in case ransomware does get installed on their networks.
Mar 25, 2016 | Cybersecurity Advice, Cybersecurity News, Network Security
Web-borne attacks on enterprises are increasing, although it is important not to forget to protect against email attacks, as shown by a recent campaign using the Olympic Vision keylogger.
Olympic Vision Keylogger Used in Recent Business Email Compromise Attacks
The attackers behind the latest campaign are using the Olympic Vision keylogger to gain access to business email accounts. Trend Micro discovered the latest campaign and was able to trace the attacks and link them to two Nigerian cybercriminals. Trend Micro determined that the current campaign has been conducted in 18 different countries including the United States.
Business email accounts contain a wealth of data, which in the wrong hands, could result in considerable damage being caused to an enterprise. However, it is not only data stored in the email accounts that hackers want to obtain. The cybercriminal gang behind the latest attacks have a different purpose. Attacks are being conducted to gain access to business email accounts to use them to send emails to account department employees instructing them to make bank transfers to the attackers’ accounts. Large transfers are often made following a business email compromise (BEC) attack.
If hackers can gain access to the email account of a senior executive, they can use that account to send messages to members of staff in the accounts or billing departments requesting transfers be made to their bank accounts. BEC is a highly effective attack strategy. If an email is sent from a CEO to the accounts department requesting an urgent transfer be made, many employees would not think twice before making the transfer as instructed.
This social engineering technique takes advantage of the fact that many employees would not question a direct request from a CEO or senior account executive. A transfer is made and the attacker receives the funds, withdraws the money, and closes the account. This often occurs before any red flags are raised, even when the transfer is for tens or hundreds of thousands of dollars.
Sophisticated Attacks Being Conducted Using Unsophisticated Malware
The Olympic Vision keylogger is not a sophisticated malware. Once installed on a device it will steal information including the computer name, Windows product keys, keystrokes, network information, clipboard text, and data saved in browsers, messaging clients, FTP clients, and email clients. It is also capable of taking screenshots.
Those data are then encrypted and are sent via email, FTP, or other means to the attacker. The Olympic Vision keylogger is capable of displaying fake error messages, and can disable computer functions to evade detection – Task Manager for example can be blocked as can registry editing tools. The Olympic Vision keylogger is capable of terminating programs that may detect it, and uses anti-emulation to prevent it running in a sandbox.
With the information collected, attackers are not only able to gain access to business email accounts, they can search for other computers, study workflows, and gather intelligence. The intel is used to construct convincing emails and ensure they are sent to individuals in the account department authorized to make bank transfers.
The attacks can be incredibly lucrative. The FBI reported recently that BEC attacks have been used by cybercriminals to obtain around $800 million dollars from businesses in the past year.
How to Protect Against BEC Attacks
There are a number of strategies that can be used to prevent BEC attacks from taking place. Software solutions can be used to prevent malware such as the Olympic Vision keylogger from being installed. SpamTitan spam filtering software can be used to block emails containing malicious attachments to prevent them from being sent to end users. If malicious emails are blocked, this places less reliance on end users not to open infected email attachments. SpamTitan can also block phishing emails, which are also used to gain access to login credentials via links to malicious websites.
Staff training is also essential. End users should receive basic security training and be advised of best practices to adopt to reduce risk. With software solutions and a culture of security awareness, the majority of attacks can be prevented.
However, it is also essential to introduce policies and procedures to prevent fraudulent bank transfers being made. A wise precaution is to introduce policies that require bank transfer requests to be authorized by a supervisor. This additional control can help to ensure fraudulent transfer requests are identified.
Any atypical request for a transfer from a senior account executive, especially those that require large sums to be transferred to accounts not previously used by the company, should be verified with the person who made the request prior to the transfer being made.
Mar 19, 2016 | Cybersecurity News, Internet Security News, Web Filtering
Cybercriminals are moving away from email attacks and are concentrating on web-based exploits to deliver malware. Email remains a major source of malware, but web-based attacks are now much more prevalent.
Web-Based Exploits Increasingly Used to Deliver Malware
A recent report from Palo Alto Networks showed that out of just over 68,000 malware samples collected, 25% were delivered via email, whereas 68% were delivered during web-browsing. Those figures were for known malware. When it comes to undetected samples, the figures for web-browsing rose to 90% compared to just 2% delivered via email. Undetected malware samples are those which are not detected by traditional anti-malware and anti-virus solutions.
It is easy to see why web-based exploits are being favored by cybercriminals. It takes much longer for web-based exploits to be detected by anti-virus software than email-based attacks. Palo Alto reports that it takes four times as long to detect web-based exploits as it does email-based attacks. Attackers are also able to tweak web-based malware in real-time. Email-based malware needs to be sent out and changes can only be made for each new campaign.
In the case of email-based malware attacks, the malicious software is relatively easy to detect by AV companies. They are able to give each malware sample a signature, which makes it much easier to block attacks. In the case of web-based malware this is a much harder task. The malware can be tweaked in real-time, making it harder for AV companies to capture and create a signature. A web server on which malware is hosted can be configured to re-code the malware automatically and generate many thousands of unique malware. Capturing and adding a signature to each simple takes too long.
There are many methods that can be employed to reduce the risk of malware infections from web browsing, although one of the easiest preventative steps to take is to use a web filtering solution such as WebTitan. WebTitan allows organizations to carefully control the websites that can be accessed by end users.
Palo Alto reported that HTTP proxies were frequently used in malware delivery. The blocking of HTTP proxies and web anonymizers can help to improve security posture and reduce the risk of malware downloads. P2P networks are also commonly used to deliver malware, and these can also be easily blocked with WebTitan web filtering solutions.
Social media websites are a common source of malware infections. A recent survey conducted by the Ponemon Institute revealed that 18% of respondents had experienced a malware attack via social media websites. Blocking access to social media networks, or blocking the file-transfer function of Facebook for example, can help to reduce the risk of malware downloads.
The threat landscape is constantly changing; however, by carefully controlling the actions that can be performed by end users with a web filter, the risk of malware infections can be greatly reduced.
Mar 18, 2016 | Cybersecurity News, Internet Security News
A recent study conducted by the Ponemon Institute on behalf of IBM investigated web application security visibility. The report revealed for the majority of organizations there is none. When it comes to application security, many companies are in the dark and either do not test the apps they use, or do not address the vulnerabilities they discover when they do.
640 application development and security professionals were asked questions about application security and the steps being taken to secure apps. The study also aimed to get an answer to the question, how much do organizations know about the security of the applications they are using on a day to day basis?
The results of the survey are worrying. More than a third of companies (35%) perform no application security testing. Consequently, they are unaware if the apps they use have security vulnerabilities. Worse still, 69% of respondents said they were not aware of all of the apps and databases that were in use in their organization.
Application Security Visibility Needs to be Improved
The study also revealed that more than two thirds (67%) of organizations do not have overall visibility into the state of application security in their respective companies. Out of the organizations that do perform application security testing, more than half do not take steps to address security vulnerabilities they discover. 34% of respondents said urgent security vulnerabilities are not being fixed and 43% said web application security was not a priority in their organization.
When asked why thorough testing of applications does not take place, 56% of respondents said it was due to time constraints and organizational pressure to release applications quickly. 55% said that their organization’s developers are too busy to work on application security issues and 70% said they believed their organization invested too little in securing web applications and that insufficient resources were allocated to the task.
Developers do not feel that it is their job to ensure applications are secure, and that this task should be conducted by information security professionals employed by their organizations. Another issue is web application security vulnerabilities take a long time to resolve. When asked how long, 38% said that each vulnerability takes around 20 hours to address.
There is, unfortunately, not enough time to make applications secure. However, there is no shortage of attackers willing to take advantage of security vulnerabilities that remain in web applications. Unless the security of web applications is improved, those vulnerabilities could well be exploited.
Mar 17, 2016 | Cybersecurity Advice, Cybersecurity News, Social Media, Web Filtering
Enterprise social media usage policies have only been introduced by 54% of organizations according to a recent social media research study conducted by Osterman Research.
Social media use in the workplace has grown significantly in recent years, both personal use of social media sites as well as the use of the platforms for business purposes. However, just over half of enterprises have implemented policies that limit or restrict use of the websites.
Enterprises face a choice. Allow the use of the sites and accept that a considerable amount of each employee’s day will be devoted to personal social media site use, or place controls to limit use. These can be restrictions on the times that the sites can be accessed, the amount of time each employee is “allowed” to take as Facetime, or the actions that can be performed on social media sites.
There are good reasons for not introducing social media usage policies. Some employers believe social media site use can improve collaboration between employees and departments. Some employers believe social media use can help improve corporate culture and even lead to faster decision making capabilities.
However, some studies suggest that employers lose more than an hour each day per employee to social media networks. If that figure is multiplied by the 500 or more employees in an organization, it represents a considerable productivity loss.
Many employers do not mind a little time on social media sites each day, provided that usage is kept within reasonable limits. An employee cannot be expected to work productively for a full 8 hours a day, so allowing some social media time can help employees recharge before they get back to working at full speed. If an employee takes 5 minutes every hour to check their Facebook feed, it could actually help to increase the work that they perform each day.
Social Media Usage Policies Can Help Employers Manage Security Risk
Use of social media platforms is not only about time not spent working. There is a security risk associated with the use of social media networks. That security risk is considerable and the risk is growing. The Osterman Research study revealed the risk of malware delivery via social media networks is considerable. 18% of respondents said that they had had malware installed as a result of social media site use. 25% said they had experienced a malware attack where they could not determine the origin. Some of those incidents may have also resulted from social media site use.
Social media site use may have benefits, but it is important for enterprises to manage the risks. To do that, social media usage policies are likely to be required along with technological controls to help enforce those policies.
Osterman Research suggested a three step approach should be taken. Before enterprises implement social media usage policies it is important to find out why social media platforms are being used and how often they are being accessed. An audit should be conducted to determine the extent to which sites are accessed, the tools that are being used by employees, the time spent on the sites, and the activities that take place.
This will allow organizations to determine the benefits they get from social media site use and weigh these up against the risks. Appropriate social media usage policies can then be developed.
Employees will need to be trained on appropriate social media usage. Employers have the right to monitor Internet activity at work. The use of Facebook, Twitter, LinkedIn and other social platforms is therefore not private. Employers should explain that they have the right to monitor social media usage at work and take action against individuals who violate social media usage policies.
Osterman suggests that technologies should be implemented to control social media usage to help mitigate the risk of malware downloads and other social media threats.
Controlling Social Media Usage at Work
WebTitan Gateway – and WebTitan Cloud for WiFi – can help in this regard. Both web filtering solutions can help organizations control the use of social media sites at work and both solutions can be used to enforce social media usage policies. Controls can be placed on when social media sites can be accessed: Outside working hours or during lunch hours for example. Controls can also be set by user group. The marketing department will require a different set of rules to the billing department for example.
Controls can also be implemented to manage risk from malware. The downloading of risky files can be blocked: .exe, .scr, .zip, or .bat for example. Links to malicious websites are often uploaded to social media networks. WebTitan can be configured to prevent those sites from being accessed. WebTitan also allows Internet usage to be carefully monitored.
Many organizations prefer to take a reactive approach to social media use at work, and only introduce controls when there has been a malware attack, a breach of confidentiality, or when site usage has reached unacceptable levels. Taking a more proactive approach can prevent problems before they occur.
Mar 5, 2016 | Cybersecurity News
As if IT security professionals didn’t have enough to worry about, Skycure has uncovered a new accessibility clickjacking proof of concept malware that could be used to spy on corporate and personal emails, as well as steal corporate data stored on mobile devices.
The malware could be used to spy on all activity on an infected device, from recording emails composed via Gmail to details entered into website forms, mobile banking apps, corporate CRM systems, or messaging apps. In contrast to many mobile malware, this form does not require rooting the device and does not need many app permissions. The footprint left by the malware is incredibility difficult to identify and the user is unlikely to be aware that their device has been compromised.
Clickjacking, also known as a UI redress attack, is the act of fooling a user into clicking on a hyperlink that is hidden in an interface underneath seemingly legitimate content. A user could be playing a mobile game and clicking on parts of the screen, yet unbeknown to them, would also be giving authorizations to a malicious mobile application. That could include any number of permissions, or could be used to authorize a download of malware onto the device.
A typical example of clickjacking is where an attacker uses a fake X button which the user clicks to close an advert. If the X also closes a dialog box or an advert, the user is unlikely to be aware that anything untoward has occurred. Yet that X could also trigger a download or give a malicious app permission to access the microphone or all text entered on the device.
Android 4.4 and Below Susceptible to Accessibility Clickjacking
Accessibility clickjacking takes advantage of accessibility APIs, which were introduced in Android 1.6. The purpose of accessibility APIs is to make Android easier to use for people with disabilities, such as the visually impaired. The benefit is the APIs can perform a number of actions so the user doesn’t have to, but that is also the problem. These APIs have access to system-wide tools, and can interact with numerous interfaces. While these APIs are certainly beneficial, they are a potential security risk that can be exploited.
The accessibility clickjacking PoC malware identified by Skycure takes advantage of accessibility APIs, and by doing so can record virtually all activities performed on the device and perform actions without users’ consent.
The example provided involves a game that takes advantage of the accessibility feature, and gets the user to click on certain parts of the screen to progress to the next level. When a click is performed it gives a permission via the underlying software. In the example it gives an application permission to record all keystrokes entered via the Gmail app.
The researchers have warned that not only can this technique be used for keylogging, but a hacker could also use the technique to change admin settings, disable functions, encrypt the device, or delete files. All Android devices except 5.x and above are susceptible to accessibility clickjacking. That is 65% of all Android phones currently in circulation.
Mar 4, 2016 | Cybersecurity News
Researchers at Kaspersky Lab say the recently discovered Android Triada Trojan is one of the most sophisticated Android malware variants yet to be discovered and that it rivals Windows-based malware for complexity. 6 out of 10 Android devices are estimated to be vulnerable to attack by the Triada Trojan. As if that is not bad enough, the malware runs silently and embeds itself in the Android system making it virtually impossible to detect. Nikita Buchka, a junior malware analyst at Kaspersky Lab, said “Once Triada is on a device, it penetrates almost all the running processes, and continues to exist in the memory only.” All of the processes remain hidden, both from the user and application.
It has been discovered in the wild and has primarily been use to infect devices in Russia and Ukraine, suggesting that’s where its authors are based; although it has also been found in India and various other APAC countries. The malware is believed to infect devices via app downloads, in particular those downloaded from untrusted sources rather than the Google Play store. That said, in some cases infected apps have been found in Google Play app store.
Kaspersky Lab researchers say the malware has been developed by “very professional” cybercriminals and suggest the developers are extremely experienced hackers with a deep understanding of the Android platform.
Triada Trojan Capable of Monitoring All Phone Activity
The Triada Trojan is capable of gaining access to all apps running on an infected device and can change the code of the app and monitor all activities on the phone. The malware can intercept SMS messages and reroute them, which is how the researchers believe the malware will make its developers money. They say the malware is likely being used to reroute in-app purchases and direct the funds to the attackers’ accounts.
Not only is the Triada Trojan almost impossible to detect with the majority of Android anti-virus and anti-malware programs, even if it is detected, removing the Triada Trojan from an infected device is exceptionally difficult. Standard removal techniques will not succeed in ridding the device of all elements of the Triada Trojan. To disinfect an infected phone, the user has to jailbreak the Android system and manually remove all of the components.
The new malware can only infect Android 4.4.4 Kitkat and below; however even though two new Android versions have since been released, the majority of Android devices run on Kitkat or earlier versions. 30% of devices run on version 4 or below, and those devices are particularly vulnerable to attack.
Kaspersky Lab researchers have previously warned that Trojans that gain superuser privileges and are being used to display advertising or install apps would eventually be used for far more malicious activities such as rooting malware. 11 different Android malware families are known to gain root access, and three of them work together – Ztorg, Gorpo and Leech. Those malware have collectively been identified as Triada.
The malware uses Zygote to launch application processes, which until the discovery of Triada, was only known to be possible as a proof of concept, and had not been exploited in the wild.
The researchers say that the new “Triada of Ztrog, Gorpo and Leech marks a new stage in the evolution of Android-based threats.”
Mar 3, 2016 | Cybersecurity News, Internet Security News, Network Security
A new report released by the Ponemon Institute suggests data breaches caused by mobile devices are not as rare as previously thought. Last year, Verizon released a data breach report suggesting that while mobile malware is increasing, it is not yet a major threat for attacks on organizations. Attacks are conducted, but they tend to target individuals.
Are Corporate Data Breaches Caused by Mobile Devices?
Verizon determined that only 1% of data breaches use mobile devices as an attack vector. The Ponemon report suggests the figure is far higher, with 67% of respondents claiming the use of mobile devices by employees was certain or likely to have resulted in a beach of sensitive corporate data.
The Ponemon study, which was commissioned by security firm Lookout, set out to cast some light on enterprise mobile security risk. 588 IT security professionals employed by Global 2000 companies in the United States were asked about the threat from mobile devices.
The report suggests there is a disconnect between IT departments and employees when it comes to the data that can be accessed using mobile devices. Many IT departments have implemented controls to limit data access via BYOD or corporate devices. However, employees still appear to be able to access corporate data none the less
The study found significant discrepancies between the data IT departments said could be accessed, and the responses provided by employees. For instance, when both groups were asked about whether confidential or classified documents could be accessed, 33% of employees said access was possible compared to just 8% of IT security professionals. 19% of IT security professionals said mobile devices could not be used to access customer data, yet 43% of employees said the data were accessible via their mobiles.
IT departments must therefore implement better controls to ensure mobile devices cannot be used to access sensitive data, or employees must be trained on the potential risks from using their mobile devices. Policies would also need to be developed to dictate what mobile devices can and cannot be used for.
The Average Infected Mobile Device Costs Organizations $9,485
The report also looked into the cost of data breaches caused by mobile devices. The average infected device was estimated to cost an organization an average of $9,485.
According to the report, mobile malware infections are a real concern. For any given company, many of the devices in use are already be infected with malware. The study suggested that “Of the 53,844 mobile devices in the average Global 2000 enterprise, 1,700 of those devices are infected by malware at any given time.”
When asked about the protections put in place to manage data access by employees, many companies had already implemented a number of safeguards to keep corporate data secure.
47% of organizations used whitelists and blacklists, 40% used mobile device management, while 45% used identity management. However, more than 4 out of 10 respondents said that none of those security measures were used by their organizations.
With the threat from mobile malware high, organizations need to devote more time and resources to mobile device security. Fortunately, this appears to be the case. The Ponemon report indicates that mobile security budgets are increasing and will represent 37% of the IT security budget next year. A considerable improvement on the current 16%.
Feb 25, 2016 | Cybersecurity News
The source code of a nasty Android banking malware has been leaked via underground forums by an individual who appears to have purchased the malware from the developers. The malware is known by many names, although GM Bot is one of the most common. Others include Slempo, Bankosy, Acecard, and MazarBot.
The code, which was encrypted, was posted on an underground forum and the poster said he would be willing to supply the password to decrypt the file to anyone who asked him, provided they were active members of the forum. He appears to have made good on the offer, although someone else appears to have distributed the password to other individuals. With a number of individuals now in possession of the decrypted file, more attacks using GM Bot can be expected. The source code was previously being sold for $500 via banking
The malware family works using activity hijacking and can be used to attack users of Android 4.4 and below. The malware cannot be used on versions 5 and above, although that does mean that 65% of devices currently in use are susceptible GM Bot android banking malware attacks.
Android Devices Running KitKat and Below Susceptible to The Android Banking Malware
Activity hijacking is a technique used to log activities performed on a compromised device. In the case of this Android banking malware, it is used to record the login credentials entered into mobile banking apps. The user of a compromised device launches a banking app and enters their credentials; however, the malware uses an overlay above the actual app and all input is recorded and transmitted to the hacker.
This Android banking malware is also able to intercept SMS messages, enabling the hackers to hijack authentication codes sent to the user’s device. The malware can also forward phone calls allowing hackers to bypass other security protections used by banks. Data can also be deleted from a compromised device, and it can also capture data entered via websites via the Chrome browser. This Android banking malware is also known to lock users’ devices giving attackers the time they need to pull off banking fraud.
Security experts are predicting a wave of new attacks using GM Bot, but since the hacker also posted details of how it can be installed and supplied a tutorial, hackers could use the information to develop new Android banking variants.
Feb 24, 2016 | Cybersecurity News, Internet Security News, Network Security
Security vulnerabilities in wireless devices can be exploited by hackers, but what about mousejacking wireless mice and hijacking wireless keyboards? According to a team of security researchers at Bastille, an IoT security start-up, the devices can be hijacked and used by hackers to steal data or compromise a network. Furthermore, in many cases the devices can be hijacked from up to 330 feet away. That’s far enough away for a hacker to be able to sit in his or her car outside a building and force a user to download malware. All a hacker is likely to need is about $15 of very readily accessible hardware say the researchers.
Mousejacking – A New Concern for Security Professionals
Bastille’s researchers looked at wireless mice and keyboards from major device manufacturers such as Logitech, Microsoft, Lenovo, HP, and Gigabyte. Since alerting the manufacturers to the risk of mousejacking and keyboard-jacking, some have released patches to address the vulnerabilities. For others, no patches have yet been developed leaving the devices vulnerable to attack. The problem does not appear to affect Bluetooth devices, but all other mice and keyboards that use a wireless dongle are potentially vulnerable.
With basic hardware, including a software-defined radio, a hacker could scan for the frequencies used by wireless devices and identify targets. Once a target was identified, forged packets could be transmitted to the address of the target.
While traffic sent between a wireless keyboard or mouse and the device’s dongle is encrypted, the dongle can still accept unencrypted commands, provided those keystrokes or clicks appear to come from its accompanying wireless mouse or keyboard. The researchers were able to inject keystrokes by sending unencrypted packets via the dongle that pairs with its wireless device.
Mousejacking could potentially be used to download malware onto devices, although Bastille software engineer Marc Newlin has hypothesized that the flaw could be used by a hacker to set up a wireless hotspot on the device. That hotspot could then be used to exfiltrate data, even in the absence of a network connection. A command window could also be opened on the device and a network vulnerability introduced, or a rootkit could be installed.
Logitech has already issued a patch and Lenovo has addressed the vulnerability for all new devices, but its patch cannot be applied to existing devices and must be installed at the time of manufacture. Microsoft is looking into the reported vulnerability but a patch has not yet been issued. Some Dell devices can also be patched, but not all.
While an mousejacking attack would be complicated and difficult to pull off outside of a controlled environment, a skilled hacker in close proximity to a device could potentially conduct a mousejacking attack. Since mousejacking can be used up to 330 feet away from the device, that individual would not even need to be in the building.
Feb 22, 2016 | Cybersecurity News, Network Security
A hacker has compromised the official Linux Mint website and has linked the official Linux Mint ISO to a modified version hosted on a server in Bulgaria. The modified ISO contains malware that will allow the hackers to take control of the machines on which Linux Mint is installed. The Linux Mint cyberattack has impacted all individuals who downloaded the ISO on 20th February.
The ISO included an IRC backdoor that will allow attackers access to all infected systems. The Linux Mint ISO hack was achieved by modifying a PHP script on the WordPress installation used on the site.
The Linux/Tsunami-A malware connects to an IRC server and can receive instructions from the hacker behind the attack. The machine on which the malware is installed could be used as part of a DDoS attack, or the machine could have further malware downloaded to it.
The backdoor had been installed in the 64-bit version of the Linux Mint 17.3 Cinnamon edition. While the 32-bit version does not appear to show any sign of an infection, the hacker responsible appears to have been attempting to install a backdoor in that ISO as well, as that file was also stored on the attacker’s server. The hacker responsible was reportedly trying to construct a botnet, although Mint Protect Leader Clement Lefebvre has said that the intentions of the hacker are not fully understood.
The names of three individuals who are believed to be involved in the Linux Mint cyberattack have been obtained by Lefebvre’s team. They are associated with the website on which the modified ISO was hosted, although it is not clear at this stage whether an investigation into those individuals will be launched. That will depend on whether any further action is taken by the hacker, according to a blog post by Lefebvre.
Linux Mint Cyberattack Compromised 71,000 User Accounts
In addition to linking to a modified version of the ISO file, the forum database on the Linux website has also been compromised. The account details of all 71,000 individuals registered on the forum have been exposed. That database has been listed for sale for a reported 0.197 Bitcoin according to ZDNet.
Fortunately, the Linux Mint cyberattack was discovered quickly and action taken to prevent further malicious copies of the ISO being downloaded. The Linux website has been taken offline while the issue is fixed.
All individuals who downloaded the ISO from the official website have been advised to check to see if their version has been hacked. It is possible to determine whether the ISO has been hacked by checking its MD5 signature by running “md5sum yourfile.iso”, using the name of the downloaded ISO and checking this against the valid signatures posted on the Linux Mint website.
All individuals who have an account on forums.linuxmint.com have had their username, email address, private messages, and encrypted copies of their password exposed. Users have been advised to change their passwords immediately.
Feb 21, 2016 | Cybersecurity Advice, Cybersecurity News, Social Media
Nothing is certain in life apart from death and taxes, apart from tax season phishing scams which have started particularly early this year. Inboxes are already being flooded with phishing emails as cybercriminals attempt to file tax returns early. Not their own tax returns of course, but fraudulent claims on behalf of any email recipient who divulges their Social Security number and personal data to the scammers.
Tax season phishing emails are sent out in the millions in the run up to the April 15, deadline. If a tax refund can be submitted before the victim, the criminals will receive the refund check.
How to Spot Tax Season Phishing Scams
Each year tax fraudsters develop new and ever more convincing phishing scams to get taxpayers to divulge their personal data and Social Security numbers. With these data, fraudsters can submit fake tax returns in the names of the victims.
While phishing emails can be easy to spot in some cases, the fraudsters are now getting much better at crafting official looking emails that appear to have been set from the IRS.
The emails use the same language that one would expect the IRS to use and the email templates use official logos. The emails contain links that have been masked to make the email recipient think they are being taken to an official website. Clicking on the link will fire up a browser window and the soon-to-be-victim will be taken to a website that looks official.
Visitors will be asked to update their personal information, add their Social Security number, or even be requested to divulge their Self-Select PIN for the online tax portal. Divulging these data is almost certain to result in tax fraud.
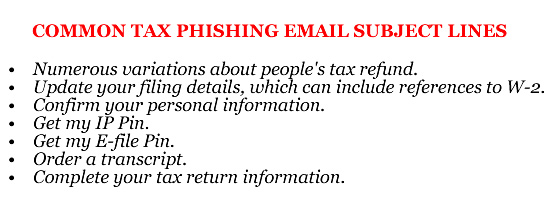
Tax Season Phishing Emails Are A Growing Concern
Taxpayers have been warned to be ultra-cautious. More tax season phishing scams have been identified this year than in previous years, with tax-related phishing and malware scams up 400% year on year.
IRS Commissioner John Koskinen warned that “Criminals are constantly looking for new ways to trick you out of your personal financial information so be extremely cautious about opening strange emails.”
Tax season phishing scams are not only conducted via email. In fact, phone scams have previously been one of the commonest ways that criminals obtain the information they need to submit fraudulent tax returns; however, the use of phishing emails is growing.
For the 2014 tax year, the IRS received 1,361 reports of phishing and malware schemes in the run up to the April deadline. That total has already been surpassed and February is not yet over. 1,389 reports have already been received. The January total was 254 higher than for the 2014 tax year, with 363 incidents reported by February 16, which is 162 more than the total for the entire month of February last year.
IRS Tax Season Phishing Emails Used to Deliver Malware
While criminals are attempting to phish for personal data, that is not the only consequence of clicking on a malicious link. The websites used by the cybercriminals behind these phishing scams are loaded with malware. Those malware enable cybercriminals to log keystrokes on infected computers and gain access to far more data than Social Security numbers. Bank account logins and passwords can be obtained, access to email accounts, and much more.
Tax Professionals Are Being Targeted with Phishing Scams
It is not only the public that must be vigilant and on the lookout for tax season phishing scams. Tax professionals are also being targeted by cybercriminals using similar schemes. The aim is to get accountants and tax advisers to reveal their online credentials such as their IRS Tax Professional PTIN System logins.
The IRS advice is to be vigilant and report any suspected phishing email. The IRS does not typically request data via email and does not initiate contact with taxpayers via email, text message, or social media channels. If an email is received asking for a link to be clicked or an attachment to be opened, it is likely to be a scam and should be reported to the IRS.
Feb 19, 2016 | Cybersecurity News
Palo Alto Networks has announced the discovery of the Xbot Trojan; a new mobile security threat targeting users of Android Smartphones. Not only will the malware steal banking usernames and passwords, but it can also lock users’ devices and demand a ransom to unlock them. The new family of dual action malware acts as both a Trojan and ransomware, and is a double whammy for anyone who inadvertently downloads it to their Android phone.
Xbot Trojan Family Capable of Multiple Acts of Maliciousness
The new Xbot Trojan, which is believed to be of Russian origin, is capable of phishing for bank account information, targeting specific banking apps and conducting phishing attacks on users of Google Play. It displays fake notifications using the Google Play logo asking users to add in payment information, mimicking that used by the official Google Play app.
Clicking on the notification will download a webpage asking users to enter their credit card number, expiry date, CVV number as well as the name of the card holder, their registered address, phone number, and a verified by via number or Mastercard SecureCode. The Xbot Trojan is also capable of intercepting two-factor authorization SMS messages.
So far, Palo Alto has discovered fake webpages used by the malware to target customers of 7 different Australian banks, with the login interfaces closely mimicking those used by the legitimate apps. Users are asked to enter in their ID numbers and passwords. The malware does not compromise the legitimite banking apps, only mimics their interfaces.
The C2 contacted by the malware can decide which faked app webpage to display, so it could easily be adapted to target other banks in other countries.
Additionally, the Xbot Trojan is capable of encrypting the device on which it is installed. It displays an interface using WebView suggesting the device has been locked with CryptoLocker, and demands a ransom of $100 to unlock the device. The ransom must be paid via PayPal MoneyCash Card within 5 days.
While the interface says that the user has no alternative but to pay the ransom to unlock the encrypted files, the encryption used is not particularly robust and files could potentially be recovered without paying the ransom.
The Xbot Trojan is also an information stealer and can collect and exfiltrate phone contacts to its C2 server. It can also intercept all SMS messages that are sent following its installation.
Xbot Trojan is the Latest Incarnation of Aulrin?
The Xbot Trojan uses activity hijacking, which is the launching of a malicious activity instead of the intended one when a user attempts to open an app. While the user will believe they are using the correct application, such as a banking app, they will actually just be handing over their banking credentials to the hackers behind the malware. So far, Palo Alto has discovered 22 Android apps in the new Xbot Trojan family.
Palo Alto researchers believe the malware is a successor to the Aulrin Trojan, which first appeared in 2014. While both Trojans contain some of the same resource files, and have similar code structures, their modes of action differ. Aulrin used the .NET framework and Lua, whereas the Xbot Trojan uses Javascript via Mozilla’s Rhino framework. Palo Alto researchers believe that the Aulrin malware was simply rewritten in a different language.
The first samples of the malware appeared in late spring last year, but since then new variants have appeared that are increasing in complexity, making them harder to detect.
The good news, unless you live in Russia or Australia, is the infections have so far been confined to those countries. The bad news is that the malware’s flexible infrastructure means it could very easily be adapted to target other Android apps.
Feb 17, 2016 | Cybersecurity News, Internet Security News, Network Security
A Google engineer has accidentally discovered a critical glibc security vulnerability that has existed since 2008. After committing several hours to hacking the vulnerability, Google engineers managed to come up with a fully working exploit that could be used to remotely control Linux devices. The glibc security vulnerability has been compared to the Shellshock security vulnerability uncovered in 2014 due to sheer number of hardware devices and apps that could potentially be affected.
The security vulnerability came as a surprise to Google engineers who were investigating an error in an SSH application which caused a segmentation fault when trying to access a specific web address. It was only after a detailed investigation that they discovered the fault lay with glibc.
Maintainers of glibc were contacted and alerted to the security vulnerability, but as it turns out they were already aware of the issue. It had been reported in July 2015 but had not been rated as a priority. That said, when Google contacted Red Hat, they confirmed they too had discovered the flaw and were working on a patch.
Linux Devices at Risk from Critical Glibc Security Vulnerability
While Windows, OS X, and Android devices are unaffected by the glibc security vulnerability, hundreds of thousands of hardware devices could potentially be affected. The security flaw affects most distributions of Linux and thousands of applications that use GNU C Library source code. All versions of glibc above 2.9 are affected.
The code is used for Linux distributions used for a wide range of hardware, including routers. The vulnerability is a buffer overflow bug in a function that performs domain lookups: getaddrinfo()
If hackers managed to replicate Google’s exploit they would be able take advantage of the vulnerability and remotely execute malicious code. The security vulnerability could be exploited when unpatched devices make queries to domain names or domain name servers controlled by attackers.
Google engineers have been working with Red Hat to develop a patch to address the vulnerability, and by combining knowledge of the vulnerability they have been able to develop a fix for the flaw, and a patch has now been released. It is essential that the patch is applied as soon as possible to ensure that the vulnerability cannot be exploited.
Updating to the latest version of glibc may be a fairly straightforward process. Linux servers can be patched by downloading the update, although things may not be quite so straightforward for some applications, which will need to be recompiled with the new library code. This could potentially result in a number of devices remaining vulnerable for some time.
Now that the vulnerability has been announced, hackers will be attempting to develop an exploit. Google has published a proof of concept, although obviously not full details of its weaponized exploit. The exploit is apparently not straightforward, which should buy Linux administrators a little time and allow them to check systems and ensure that affected hardware devices are patched.
Feb 4, 2016 | Cybersecurity News, Internet Security News, Network Security
Two highly serious Netgear NMS300 ProSafe security vulnerabilities have been discovered that could be exploited by hackers to gain control of servers running the software, and/or download any file on the server on which the software is running.
The Netgear NMS300 ProSafe network management system is used by many companies to configure and monitor their network devices. Netgear NMS300 ProSafe is popular with small to medium size businesses as the software is free to use on fewer than 200 devices.
Recently Agile Information Security researcher Pedro Ribero discovered two critical Netgear NMS300 ProSafe security vulnerabilities.
Netgear NMS300 ProSafe Security Vulnerabilities
One of the vulnerabilities (CVE-2016-1525) allows remote code execution by an unauthenticated user via the Netgear NMS300 web interface. A hacker would be able to exploit this security flaw and upload and run java files with full system privileges, potentially gaining full control of the server on which the software is being run.
The NMS300 system is used to manage a wide range of networked devices such as routers, switches, network-storage devices, wireless access points and firewalls. Not only could this vulnerability allow the configuration of these devices to be changed, it would also permit an attacker to install firmware updates on those devices.
The second vulnerability (CVE-2016-1524) discovered by Ribeiro is an arbitrary file download, that would permit an authenticated user to download any file stored on the server that is being used to run NMS300.
These Netgear NMS300 ProSafe security vulnerabilities are particularly serious and at the present time there is no patch available to plug the security flaws. Users can improve protection and prevent the Netgear NMS300 ProSafe security vulnerabilities from being exploited by restricting access to the web interface with new firewall rules to limit access. Ribeiro recommends never exposing Netgear NMS300 to the Internet or untrusted networks.
Both vulnerabilities affect Netgear NMS300 versions 1.5.0.11, 1.5.0.2, 1.4.0.17 and 1.1.0.13

