Cybersecurity Advice
Our cybersecurity advice section provides comprehensive information about the latest online security threats – not only the threats from unfiltered spam emails, but also the risks present on the Internet from malvertising and vulnerable websites onto which malware exploit kits may have been loaded by cybercriminals.
We also provide advice on the precautions that can be taken to heighten cybersecurity defenses and mitigate the risk of inadvertently downloading an infection. The message throughout all of our cybersecurity advice is to protect your network and WiFi systems with an email spam filter and web content control solution.
Jan 17, 2017 | Cybersecurity Advice
If you use a computer, you are at risk of having your device infected with malware; however, listed below are some useful tips for preventing malware infections.
Unfortunately, signature-based anti-malware software is far less effective at preventing infections than in years gone by. Malware developers are now using a wide range of strategies and techniques to prevent traditional anti-malware solutions from detecting and blocking infections.
Rely on anti-malware or anti-virus software alone and sooner or later you may find your device has been compromised, your keystrokes are being logged, and your – or your organization’s – data are being stolen.
However, there are some straightforward strategies that you can adopt to prevent malware infections and keep your computer, and your network, malware-free.
10 Tips for Preventing Malware Infections
Backup Your data
OK, a data backup will not prevent a malware infection, but it can help you recover if your computer is infected with ransomware or if your data are corrupted as a result of an infection – or removal of malware. The only way to recover from some infections is to wipe out your system and restore it from a previously known safe point. You must therefore have a safe point that you can use. Nightly backups should be performed. You only then stand to lose 24 hours of data at most.
Keep your malware definitions up to date
Anti-malware software may not be as effective as it once was, but you do need to give it a fighting chance. If you do not keep your definitions 100% up to date you are asking for trouble. This may sound obvious, but many organizations delay updating malware definitions for forget to set software to update automatically on all devices.
Never click on links or open email attachments from unknown senders
Cybercriminals target employees as it is far easier to gain access to a corporate network if an employee bypasses their organization’s defences and installs malware. All it takes is for one employee to install malware for attackers to gain a foothold in a network. Ensure that all employees receive anti-phishing training and have at least basic IT security skills. Most data breaches start with a phishing email.
Ensure operating systems and software are patched promptly
Operating systems, firmware, and all software must be kept up to date. As soon as patches are released, cybercriminals will be reverse engineering them to uncover the vulnerabilities. Don’t delay applying patches. Good patch management policies are essential for preventing malware infections.
Watch out for shadow IT
Downloading pirated software is an excellent way to infect computers with malware. Pirated software is often bundled with malware, spyware, and all manner of nasties. Block the running of executables and keygens if practical. Only install software from trusted sources. As an additional check, before installing software, check the software provider’s MD5 hash against your copy. If it’s a match, install. If not, delete.
Take care with USB drives
Not all malware comes via the web or email. USB drives can easily introduce malware. Make sure your anti-malware solution is configured to automatically scan USB drives before granting system access and never plug in a drive from an unknown source.
Perform regular malware scans
Having anti-virus and anti-malware software will not necessarily mean your system is protected. Full system scans should still be performed. Some infections can slip under the radar. A full scan should be performed at least once a month.
Keep abreast of the latest malware trends
You may have limited time, but it is important to keep abreast of the latest attack trends, cyberattacks, data breaches, and threat reports. Check the warnings from US-CERT, and monitor websites such as DarkReading, CIO, CISO, and The Register. A little research goes a very long way.
Keep mobile devices protected
Mobiles can easily be used to introduce malware onto networks to which they connect. Mobiles are often used on unprotected Wi-Fi hotspots, and the devices are increasingly being targeted by hackers. Ensure security software is installed on mobile devices and security settings on phones are active.
Use a firewall, web, and Wi-Fi filtering
A firewall is essential tool for preventing malware infections, although businesses should consider purchasing a next generation firewall device. Next generation firewalls combine a traditional firewall with other network device filtering functionalities. Web and Wi-Fi filtering solutions are also important. By filtering the Internet, it is possible to prevent drive-by malware downloads and carefully control the risks that employees take.
Dec 30, 2016 | Cybersecurity Advice, Network Security, Web Filtering
Cybercriminals have embraced ransomware and have been increasingly targeting businesses, yet many business leaders are unsure how to prevent ransomware attacks. Consequently, the risk from ransomware is not being effectively managed, and that may prove costly.
Ransomware is a form of malware that is capable of encrypting files on local machines, network drives, and servers. Any computer that is connected to the Internet can potentially be infected. Even without internet access, files may be encrypted if a computer is networked. The latest ransomware variants are capable of spreading laterally within a network and encrypting the data on hundreds of devices.
Files required for critical business processes may be encrypted and made inaccessible. A successful attack can result in a company’s operations grinding to a halt. A healthcare ransomware attack can result in patients’ health information becoming inaccessible. An attack on a pharmaceutical company may result in files necessary for drug manufacture being locked, which could affect the quality of products. Lawyers offices may lose essential client information. Few businesses could continue to operate at their full potential during a ransomware attack.
The loss of files can prove extremely expensive, far less than the cost of any ransom payment. Many companies therefore are left with little alternative but to pay the ransom demand. Ransom payments are actually made surprisingly frequently. According to a recent study conducted by IBM, 70% of businesses that experienced a ransomware infection ended up paying the attackers to supply the keys to unlock their data. Half of those businesses paid more than $20,000 while 20% paid more than $40,000.
Even when the ransom is paid there is no guarantee that a viable key will be supplied to unlock the encryption. Files may therefore be lost forever. One healthcare organization in the United States recently discovered that files can all too easily be lost forever. Three months after ransomware was installed on one of its servers and critical patient health information was encrypted, Desert Care Family and Sports Medicine has still not been able to unlock the encryption nor access its patients’ data.
It is essential to learn how to prevent ransomware attacks and to implement appropriate defenses not only to stop attackers from installing ransomware, but to ensure a system is put in place that will allow data to be recovered without having to resort to paying a ransom.
Recovering from a ransomware attack can be extremely expensive. Ransom payments can be extortionate. Business can be lost while systems are taken out of action. Even applying keys that have been supplied by attackers can be long winded. Each encrypted device has its own key, and those keys must be applied very carefully. A forensic analysis is also important after a ransomware attack to search for backdoors that may have added, as well as to determine if data have been stolen. Additional protections then need to be put in place to prevent future attacks from occurring.
How to Prevent Ransomware Attacks
The first and most important step to take will not prevent ransomware attacks, but it will help you to recover from a ransomware attack promptly without having to resort to paying the ransom. Recovery will depend on you having a viable backup of your data. Total file recovery may not be possible, but it should be possible to recover the vast majority of your files.
For that to be possible, you must ensure that all files on all devices and network drives are backed up. That includes all removable drives such as flash drives. Backup files must be stored on a non-networked drive, in the cloud, or ideally on an air-gapped device – One that is unplugged as soon as the backup is performed. Multiple backups should ideally be made with one copy stored in the cloud and one on a detachable storage device. You should always store backups in multiple files. If one becomes corrupted, you will not lose all of your data.
- Avoid the use of administrator accounts with extensive privileges as far as is possible. If an administrator account is required, use it and then change to a guest account with limited privileges. This will reduce the damage caused if the user’s machine is infected.
- Ensure that all software is kept up to date and your organization employs good patch management practices. In particular, ensure browser and plugin updates are applied promptly. Vulnerabilities can all too easily be exploited and used to download ransomware.
- If plugins are not required, remove them. Adobe Flash in particular, but also Java and Silverlight. If required, they should require activating individually as and when needed.
- Ensure employees’ computers are configured to show file extensions. If full file extensions are displayed, it is easier to identify potentially malicious files with double extensions.
- Ensure macros are disabled on all devices. At the very least, ensure macros do not run automatically.
- Disable Remote Desktop Protocol (RDP) on all devices unless it is absolutely essential.
- A web filter can be used to prevent end users from visiting malicious websites where ransomware can be downloaded. A web filter can also block malicious third party adverts (malversting).
- End users should be instructed never to open files from unknown senders or to click on links contained in emails unless 100% sure that the links are genuine.
- The use of a spam filter is strongly advisable. The spam filter should be configured to aggressively block threats. Executable file attachments should also be automatically quarantined.

Oct 14, 2016 | Cybersecurity Advice, Web Filtering
There are a number of reasons why ransomware attacks have been increasing and why the crypto-ransomware has now become one of the biggest and most worrying threats. However, the main reason is ransomware is extremely profitable.
How profitable? According to a recent security report from McAfee Labs, one single ransomware author managed to pull in an incredible $121 million in ransomware payments in the first six months of 2016. Take off the expenses incurred and the author cleared $94 million in profit.
That was just one author. There are many. There are now more than 200 different ransomware families and many more variants of each. Fortunately, developing new ransomware is a complicated business that requires considerable programming skill. Unfortunately, there are many individuals who rent ransomware to conduct campaigns and take a cut of the profits.
The explosion in use of ransomware in the past two years is a cause for concern for all Internet users, especially for business owners. Unfortunately, the ransomware crisis is unlikely to be resolved any time soon. As long as it is profitable, the attacks will continue. Vincent Weafer, VP of Intel Security’s McAfee Labs, expects the revenues from ransomware infections in 2016 will be of the order of several hundreds of millions of dollars and most likely considerably more.
McAfee recorded 1.3 million new ransomware samples in the first half of 2016. The risk of infection with ransomware has increased as authors employ increasingly sophisticated methods of evading detection. Ransomware is also spreading faster and encrypting even more data to ensure victims have no alternative but to pay up.
But how is it possible to prevent ransomware attacks? Unfortunately, there is no silver bullet. Prevention requires several different strategies to be adopted. To prevent ransomware attacks, check out the ransomware protection tips below.
Ransomware Protection Tips
We have listed some ransomware protection tips below that will help you to avoid ransomware infections – And how to avoid paying a ransom should the unthinkable happen.
The first rule of ransomware avoidance is backing up your data
The no More Ransom Project is a great initiative. When ransomware variants are cracked and decryptors developed, they are being uploaded onto the No More Ransom site. Victims can then decrypt their files for free. However, there are more than 200 ransomware families and less than 10 free decryptors. You don’t need to have majored in mathematics to work out that the probability of a decryptor being available is rather small. If you want to be able to avoid paying a ransom you must have a viable backup of your data.
The second rule of ransomware avoidance is backing up your data
Without a backup, you will need to pay the ransom if you want your data back. You therefore need to make sure you have a viable backup file. However, multiple backups should be performed. You should have a backup on an external hard drive and a second backup in the cloud. Your external drive must also be disconnected once the backup has been performed.
Keep software up to date
Vulnerabilities are constantly being discovered and patches issued to plug security holes. Even if exploits have not been developed to take advantage of those vulnerabilities, patches can be reverse engineered. Once patches are released, it will only be a matter of time before exploits are developed. It is therefore essential to apply patches and install software updates promptly. Patches should be prioritized with critical updates applied first.
Remove unnecessary software and browser plugins
If you have browser plugins installed that you never use, remove them. They are an unnecessary risk. Of particular concern are Adobe Flash, Java, and Silverlight. Vulnerabilities are regularly discovered in these plugins and for many businesses they are surplus to requirements. Remove them or at least set them to require manual activation.
Block adverts
Malvertising may not be the most common method of ransomware delivery but the risk should be mitigated nonetheless. Businesses should use an adblocker to prevent malicious adverts from being displayed. Do your employees need to see web adverts? If not, why take the risk?
Filter the Internet
Malicious websites containing exploit kits can probe for a wide range of security vulnerabilities and leverage these to silently download ransomware. WebTitan can be configured to block websites known to contain malware and block sites by category. Categories of websites known to be ‘high risk’ can be blocked, as well as sites that have no work-purpose. Blocking access to certain categories of websites can greatly reduce the risk from web-borne ransomware and malware infections.
Conduct security awareness training
Security awareness training is not just for employees. All individuals in an organization should be taught the security basics from the CEO down. Training should include phishing awareness and avoidance, ransomware and malware, and good security best practices such as never opening emails from unknown sources, not enabling macros, and avoiding clicking links in spam and suspicious emails.
Turn off macros
Macros are used in many organizations, but not by the majority of employees. Macros should be disabled on all devices unless essential, and even then, macros should be enabled manually on documents and spreadsheets if required.
Employ a robust spam filtering solution
A paid-for spam filtering solution should be installed to catch spam emails and prevent delivery. Email is one of the most commonly used ransomware delivery mechanisms. Anti-spam solutions such as SpamTitan can greatly reduce the probability of employees’ security training being put to the test.
Use anti-malware and anti-virus solutions
Employ anti-malware and anti-virus solutions that include a real-time scanning feature and set the solutions to update virus/malware definitions automatically. Full system scans should also be periodically conducted.
Jun 9, 2016 | Cybersecurity Advice, Cybersecurity News
The security threat from bloatware was made abundantly clear last year with the discovery of a Lenovo bloatware vulnerability, affecting the Superfish Adware program that came pre-installed on Lenovo laptops.
Bloatware is a term used to describe software applications and programs that are largely unnecessary, yet are pre-installed on new computer and laptops. The software programs can slow down computers and take up a lot of memory, yet offer the user little in the way of benefits. They are primarily used to update application features rather than to enhance security.
Unfortunately, these pre-installed programs have been discovered – on numerous occasions – to contain security vulnerabilities that can be exploited by malicious actors and used for man-in-the-middle attacks. They can even let attackers run arbitrary code, allow privilege escalation, or perform malicious software updates.
Now a new Lenovo bloatware vulnerability has been uncovered. This time it concerns the company’s software updater which has been found to contain a vulnerability that could potentially be exploited allowing man-in-the-middle attacks to be conducted.
New Bloatware Vulnerability Found in Lenovo Accelerator Application Updater: Uninstall Recommended
The Lenovo Accelerator Application has been pre-installed on a wide range of desktop computers and notebooks shipped pre-installed with Windows 10. In total, well over 100 different models of Lenovo notebooks and desktops have the Lenovo Accelerator Application installed. Lenovo says the application is used to speed up the launching of Lenovo applications and communicates with the company’s servers to determine whether application updates exist.
The UpdateAgent pings Lenovo’s servers every 10 minutes to check whether updates have been released. However, the application has recently been discovered to contain a security vulnerability that could be exploited by attackers. DuoLabs investigated a number of companies to check for security vulnerabilities in pre-installed software applications and found that Lenovo’s UpdateAgent was particularly vulnerable to attacks.
DuoLabs reported that the updater had “no native security,” and that “executables and manifests are transmitted in the clear and no code-signing checks are enforced.” The security flaws could allow an attacker to intercept these communications and manipulate responses, even allowing malicious software updates to be performed.
Lenovo has responded by issuing an advisory recommending all owners of the affected devices uninstall the software application. This is a straightforward task that can be performed by accessing the Apps and Features application on a Windows 10 computer, selecting the Lenovo Accelerator Application and manually uninstalling the program.
Jun 7, 2016 | Cybersecurity Advice, Cybersecurity News, Social Media
The Federal Bureau of Investigation (FBI) has issued a new security alert warning of a new wave of extortion email schemes. The alert was issued after its Internet Crime Complaint Center (IC3) started receiving multiple reports from individuals who had been threatened with the exposure of their sensitive data.
Cybercriminals are quick to respond to large-scale data breaches and use the fear surrounding the attacks to scam individuals into paying ransoms, clicking on links to malicious websites, or opening infected email attachments. In recent weeks, the Internet has been awash with news reports of major data breaches that have hit networking sites and a number of popular Internet platforms.
Major data breaches affected LinkedIn, MySpace, and Tumblr, and while the stolen data are old, hundreds of millions of individuals have been affected.
These cyberattacks occurred in 2012 and 2013, although the data stolen in the attacks have just been listed for sale online. These major data breaches had gone undiscovered until recently.
Extortion Email Schemes Threaten Exposure of Sensitive Data
Due to the volume of logins that were exposed in these attacks and the popularity of the sites, many individuals may be concerned that their login credentials may have been obtained by hackers. Cybercriminals are taking advantage of this fear and are sending out huge volumes of spam emails advising individuals that their sensitive data have been obtained.
In the emails, individuals are told that their name, address, telephone number, credit card details, and other highly sensitive data are being held and that they will be distributed to friends and family if a ransom is not paid. The attackers warn their victims that access to social media accounts has been gained and that the attackers have details of all of the victim’s social media contacts.
The scammers are also threatening to email and mail out details of credit card transactions and internet activity to friends, family, and employers, suggesting that the payment to prevent this from happening will be much lower than the cost of a divorce, and low in comparison to the affect it will have on relationships with friends and on social standing.
To stop the distribution of these data, victims are required to pay the attackers anywhere from 2 to 5 Bitcoin – Between $250 and $1,200. A Bitcoin address is sent in the email which the victims must use. This ensures the transaction remains anonymous.
After analyzing the extortion email schemes, the FBI has concluded that the attacks are the work of multiple individuals. The FBI has advised against paying the ransoms as this will only ensure that this criminal activity continues. Paying a ransom is no guarantee that further demands will not be received.
Any person receiving an email that they believe to be an extortion email scheme should contact their local FBI office and send a copy of the email with the subject “extortion E-mail scheme,” along with details of the Bitcoin address where payment has been asked to be sent.
Extortion email schemes are often sent out randomly in spam email; however, responding to an email will alert the attacker that the email account is active and is being checked. The best course of action is to ignore the email, to log into social media accounts and change all passwords, and to carefully monitor bank accounts and credit card statements. The FBI also advises individuals to ensure social media accounts are configured with the highest level of privacy settings and to be extremely careful about sharing any sensitive data online.
May 13, 2016 | Cybersecurity Advice, Network Security, Web Filtering
To reduce the risk of malware infections from websites you can avoid certain types of sites that are commonly used by cybercriminals to infect visitors. Sites containing pornography for instance, torrents sites, and online marketplaces selling illegal medication for example. However, while these sites are often compromised with malware or contain malicious code, they are far from the most common sites used by cybercriminals to infect visitors.
The unfortunately reality is that browsing the Internet and only visiting what are perceived to be “safe sites” does not mean that you will not be exposed to maware, malicious code, and exploit kits. Hackers are increasingly compromising seemingly legitimate websites to redirect visitors to sites containing exploit kits that download malware and ransomware.
Two CBS-affiliated news websites were recently discovered to be hosting malicious adverts that redirect visitors to sites containing the Angler Exploit Kit. MSN has been found to host malvertising in the past, as has Yahoo. A study conducted by anti-virus company Symantec revealed that three quarters of websites contain security vulnerabilities that could potentially be exploited to infect visitors with malware.
High Profile Websites Compromised and Used to Deliver Ransomware to Visitors
This week, two new websites were found to have been compromised and were used to infect visitors with malware.
The celebrity gossip website PerezHilton.com may cause problems for celebrities, but this week it was also causing problems for its visitors. The site attracts millions of visitors, yet few would suspect that visiting the site placed them at risk of having their computer files locked with powerful file-encrypting ransomware.
However, that is exactly what has been happening. Hackers compromised an iframe on the site and inserted malicious code which redirected visitors to a website containing the Angler Exploit Kit. Angler probes visitors’ browsers for security vulnerabilities and exploits them; silently download a payload of malware. In this case, the Angler Exploit Kit was used to push Bedep malware, which in turn silently downloaded CryptXXX ransomware onto the victims’ devices.
A second malvertising campaign was also conducted that redirected visitors to a different website. The exploit kit used to infect redirected visitors was different, but the end result was the same. A malicious payload was downloaded onto their devices.
Another well-known website was also discovered to have been compromised this week. The website of the world renowned French film production company Pathé was discovered to have been compromised. Hackers had managed to embed malicious code in one of the webpages on the site. The code also redirected users to a site hosting the Angler Exploit Kit, which similarly was used to infect visitors with CryptXXX ransomware.
How to Reduce the Risk of Malware Infections from Websites
Exploit kits take advantage of security vulnerabilities in browsers. To reduce the risk of malware infections from websites it is essential that browsers are kept up to date. That includes all browser plugins. If no security vulnerabilities exist, there would be nothing for exploit kits to exploit.
However, zero-day vulnerabilities are emerging all the time and software manufacturers are not always quick to develop fixes. Adobe was alerted to a new zero-day vulnerability a few days ago, yet they only just released a fix. During that time, the vulnerability could have been exploited using exploit kits. Cybercriminal gangs are quick to incorporate new zero-day vulnerabilities into their exploit kits and do so faster than software companies can release fixes. Ensuring all updates are installed promptly is a great way to reduce the risk of malware infections from websites, but additional measures need to be taken.
If you really want to improve your – or your company’s – security posture and really reduce the risk of malware infections from websites, you should use a web filtering solution. This is particularly important for businesses to ensure that employees do not inadvertently compromise the network. It can be difficult to ensure that all devices used to connect to the network are kept 100% up to date, 100% of the time.
A web filtering solution can be configured to block malvertising, blacklists can be used to prevent compromised websites from being accessed, and malware downloads can be prevented. Along with good patch management practices, it is possible to effectively reduce the risk of malware infections from websites.
May 11, 2016 | Cybersecurity Advice, Cybersecurity News, Internet Security News, Web Filtering
This week, patch Tuesday saw updates issued to address actively exploited security vulnerabilities in Internet Explorer, along with a swathe of fixes for a number of other critical Microsoft security vulnerabilities. In total, Microsoft issued fixes for 51 vulnerabilities this week spread across 16 security bulletins, half of which were rated as important, the other eight being rated as critical.
The updates tackle vulnerabilities in Microsoft Edge and Internet Explorer, Windows, the Microsoft .NET Framework, and MS Office; however, it is the browser fixes that are the most important. These include actively exploited security vulnerabilities that can be used to compromise computers if users visit websites containing exploit kits.
Security update MS16-051 tackles the CVE-2016-0189 zero-day vulnerability in Internet Explorer, which if exploited, would allow an attacker to gain the same level of privileges as the current user. The flaw could be used to take control of the entire system. The exploit could be used to install new programs on the device, create new accounts, or modify or delete data. The vulnerability modifies the functioning of JScript and VBScript, changing how they handle objects in the computer’s memory.
The IE security vulnerability was brought to the attention of Microsoft by researchers at Symantec, who had discovered an active exploit that was being used alongside spear-phishing attacks in South Korea. Users were being directed to a website containing an exploit kit that had been updated with the IE security vulnerability.
The MS16-052 security update tackles a vulnerability in Microsoft Edge which similarly changes how objects in the memory are handled. These two updates should be prioritized by sysadmins, although all of the updates should be installed as soon as possible. Even the important updates could potentially be exploited and used to gain control of unpatched computers.
Bulletin MS16-054 is also a priority update to patch critical vulnerabilities in Adobe Flash. Since Flash is embedded in both Edge and IE, Microsoft has started issuing updates to address Adobe Flash vulnerabilities. While these security flaws are not believed to have been exploited in the wild, it will not be long before they are included in exploit kits.
Microsoft may have fixed its actively exploited security vulnerabilities, but despite Adobe issuing patches for Acrobat, ColdFusion, and Reader on Tuesday, Flash remains vulnerable to attack. Adobe has yet to issue a patch for an actively exploited Flash security vulnerability (CVE-2016-4117) that affects version 21.0.0.226 and all earlier versions of the platform. This vulnerability has been included in exploit kits and can be used to take control of devices. In total, Adobe fixed 92 separate vulnerabilities in its Tuesday update.
Between Microsoft and Adobe, 143 vulnerabilities have been addressed this week. With hackers quick to add the vulnerabilities to website exploit kits, it is essential that patches are installed rapidly. These actively exploited security vulnerabilities also highlight the importance of using a web filtering solution to prevent users from visiting compromised websites where the vulnerabilities can be exploited.
May 6, 2016 | Cybersecurity Advice, Cybersecurity News, Internet Security News, Network Security, Web Filtering
Finding a web security service for MSPs can be a time consuming process. There are a number of solutions that allow MSPs to keep their clients protected from malware and reduce the risk from internal and external threats, yet many are far from ideal for use by MSPs.
The ideal web security service for MSPs must have a relatively low cost of ownership. Clients may be more than willing to implement a web security service to deal with the growing range of web-borne threats, but the cost of implementation is a key factor.
Many solutions offer all the necessary benefits for the client, but are not practical for use by MSPs. The time taken to install web security solutions and to configure them for each client can reduce profitability. The best web security service for MSPs need to be easy to install and maintain, and have a low management overhead.
Low cost solutions that are quick to install and easy to maintain allow MSPs to easily incorporate into existing packages to create a more comprehensive Internet security service. This can increase the value provided to clients, boost client revenue, and help MSPs to win more business and differentiate their company in the marketplace.
The ideal web security service for MSPs is available as a white label. This allows the service to be easily incorporated into existing packages. White labeling allows MSPS to strengthen their own brand image rather than promoting someone else’s.
Many providers of a web security service for MSPs fall down on customer support. If any issues are experienced, it is essential that an MSP can provide rapid solutions. Industry-leading technical support is essential.
WebTitan Cloud – A Web Security Service for MSPs That Ticks All the Right Boxes
WebTitan Cloud is an enterprise-class web filtering solution for MSPs that can be used to enforce clients’ acceptable use policies and control the content that can be accessed via their wired and wireless networks.
Our DNS-based web filtering solution allows organizations to prevent phishing, stop malware downloads, protect against ransomware and botnet infections, and block spyware and adware. Controls prevent the bypassing of the content filter by blocking anonymizer services. Encrypted web traffic is also inspected.
Implementation could not be any easier. There is no need for any hardware purchases or software downloads. All that is required is a change to the DNS to point to our servers and the Internet can be filtered in under 2 minutes.
Configuring each client to incorporate their AUPs is also a quick and easy process requiring no technical expertise. Highly granular controls ensure AUPs can be quickly and easily applied. There is no need to use on premise support teams. Everything can be monitored via the control panel from any Internet browser. There is no hardware or software to maintain and no patches to apply, reducing management overhead considerably. Cloud keys can be supplied to allow guests to bypass organization-wide content control settings, with time-limits applied to prevent abuse.
Reporting is effortless. A full suite of pre-defined reports can be generated automatically and scheduled for each client to allow Internet access to be carefully monitored.
We also offer fully white-labeled solutions for MSPs allowing logos, branding, and corporate color schemes to be easily incorporated. We are also more than happy to allow WebTitan Cloud to be hosted within an MSPs infrastructure.
What Your Customers Get
- Ransomware, malware, and phishing protection. Protection from malware, ransomware and the web-based component of phishing attacks. More than 60,000 malware iterations are blocked every day.
- A quick and easy to use DNS filter to manage and control web usage – Block malicious sites and control the web content employees and guest users can access.
- Easy to implement; Easy to use. Customer accounts are up and running within 20 minutes
- Improve network performance: A no latency DNS filtering solution that can be used to reduce bandwidth waste and abuse.
- Highly granular content filtering with flexible user policies
- Support for dynamic IP’s
- Works with any device
- Full reporting suite. WebTitan contains a comprehensive reporting suite providing automated graphical reports and extensive reports on demand.
- Fully automated updating – Does not add to your patching burden and requires minimal management while ensuring maximum security.
- Whitelists and blacklists Global whitelists and blacklists and custom categories can be configured to allow/block by full website address or by IP address
Benefits for MSPs
- Save on customer support time, hours and cost – No more costly ransomware call outs.
- Easy to deploy, manage and sell our awarded-winning cloud based web filtering solution
- Simple Integration into your existing service stack through API’s and RMM integrations
- Competitive pricing with a core focus on the SMB market.
- Generous margins and monthly billing
- White labelling – WebTitan can be fully rebranded with your logos and color scheme with us working seamlessly in the background.
- Set & forget. WebTitan requires minimal IT service intervention
- Short sales cycle – only a 14 day free trial required to test
- World class support – The best customer service in the industry with scalable pre-sales and technical support and sales & technical training
- Multi-tenant dashboard – MSP-client hierarchy enables you to keep clients separated and choose whether to manage client settings in bulk or on an individual basis
To find out more about why WebTitan Cloud is a game changing web security service for MSPs contact our sales team today!
MSP Testimonials
“WebTitan is an outstanding tool for most reliable content filtering. The monitoring feature of this specific product is quite unique that totally monitors all the process of online working and also secures all the data. Additionally, its set-up is superb easy and it can be done in just few minutes that save my time and energy as well.” Kristie H. Account Manager
“WebTitan is fairly easy to setup. It is available as a cloud based solution or on prem. You can get as simple or as complicated with your filtering as you like, it will handle most situations with ease. It has provided us with a stable web filtering platform that has worked well for us for many years. ” Derek A. Network Manager
“WebTitan is outstanding software that helps me a lot in minimizing viruses. The thing I like most about WebTitan is that it is extremely easy to use and configure. I like its clear interface. It lets us block malicious content and spam easily. It is no doubt an amazing product helping us a lot in kicking out harmful bad stuff.” Randy Q. Software Engineer
“By reducing malware-related security incidents, you’re reducing your number one uncontrollable expense: the people on your IT operations team, like your help desk techs.” MSP, Washington, US
“Web filtering is one of the, if not the greatest bang for your buck services. It’s built in anti malware has protected our clients, saving us thousands of hours of repair time I am absolutely certain.” MSP, New York, US
“a key part of our security stack as we’ve scaled to over 6,000 managed endpoints, while decreasing virus and malware related tickets by 70%.” MSP, Boston, US
“It has paid for itself many times over by reducing malware calls.” MSP, Toronto, Canada
May 5, 2016 | Cybersecurity Advice, Cybersecurity News, Internet Security News, Network Security, Web Filtering
Over the past two weeks there have been three worrying instances of the Angler exploit kit being used to infect website visitors with malware and ransomware. Cybercriminals are increasingly using exploit kits to deliver their malicious payloads and all organizations need to be aware of the risk.
Why AUPs May Not Be Sufficient to Keep Networks Secure
Many companies advise employees of the types of websites that can be accessed via work networks and which are forbidden. Typically, employees are banned from visiting pornographic websites, using the Internet for the sharing of copyright-protected material, installing shareware or other unauthorized software, and using unauthorized web applications and gaming sites.
Employees are provided with a document which they are required to read and sign. They are informed of the actions that will be taken for breaching the rules: verbal and written warnings for example, and in some cases, instant dismissal. These AUPs are usually effective and employees do heed the warnings if they value their jobs.
If an employee breaches the AUPs and accesses pornography for instance, action can be taken against that individual. It is probable that no harm will have been caused and the matter can be dealt with by HR.
However, if an employee breaches AUPs and visits a website that has been compromised with malware or installs shareware that includes malicious files, taking action against the employee will not undo the damage caused.
To better protect networks, AUPs should be enforced with a software solution. By implementing a web filtering solution, HR departments can ensure that inappropriate website content is not accessed, while IT departments can be prevented from having to deal with malware infections.
Even if AUPs are followed to the letter, malware may still be downloaded onto the network. The risk has recently been highlighted by two security incidents discovered in the past two weeks.
Legitimate Websites Compromised with Angler Exploit Kit
Last week, news emerged that a toy manufacturer’s website had been compromised and was being used to infect visitors with malware. The website had been loaded with the Angler exploit kit and was being used to silently infect visitors’ devices with ransomware.
An exploit kit is a malicious toolkit used by hackers to probe for security vulnerabilities in website visitors’ browsers. A visitor to a website containing an exploit kit – BlackHole, Magnitude, Nuclear, Styx, or Angler for example – will have their browser checked for out of date plugins such as Adobe Reader, Silverlight, Flash, or Java. If the plugins are not up to date, security vulnerabilities can be exploited to download a payload of malware. These attacks are silent and the website visitor will be unaware that their machine has been compromised.
This week, two more websites were discovered to have been hijacked and were being used to direct visitors to the Angler exploit kit. These websites were much more likely to be visited by company employees. They were the sites of two CBS-affiliated TV stations: KMOV in St. Louis and WBTV in Charlotte, North Carolina.
These news websites would be unlikely to be banned in AUPs, and few organizations would see the risk of their employees visiting these websites.
News Websites Contained Malvertising Directing Users to the Angler Exploit Kit
While the toy manufacturer’s website was directly infecting web visitors, in the case of KMOV and WBTV the attackers were using a common technique called malvertising. The websites had not been loaded with the Angler exploit kit, instead the attacks were taking place via third party adverts that were being served on the sites.
The sites contain adblocks which were used to serve advertisements via the Taggify network – a legitimate advertising network. However, a rogue advertiser had got around the controls put in place by Taggify and malicious adverts were being served.
The attackers hosted the malicious ad components – images and JavaScript- on their own servers. The malicious adverts were then served on unsuspecting website visitors. However, the rogue advertiser was also serving legitimate ads and these were displayed to web crawlers and scanners to avoid detection. Other users were served an advert that redirected them to the Angler exploit kit. If those visitors had browsers with out of date plugins, they would be infected with whatever payload the attackers chose to deliver.
Reduce Risk of Attack with a Web Filtering Solution
These three recent cases are just the tip of the iceberg. Criminals are hijacking all manner of websites and using them to host exploit kits. Legitimate websites serving third party adverts are also being targeted with malvertising.
Enforcing AUPs with a web filtering solution can help to prevent end users from visiting websites that have been compromised with malware. A web filter – such as WebTitan – can also be used to block third party advertisements from being displayed.
Unfortunately for enterprises, it is not possible to install patches as soon as they are released. Many patches require reboots, and that is not practical. The number of patches being released to plug security holes is considerable, and it takes time to patch all devices that connect to a network. Good patch management policies can reduce the likelihood of a successful attack, but they cannot prevent all attacks from taking place. If a web filtering solution is used that can block malvertising and websites known to contain malware, end users and networks will be better protected.
Apr 30, 2016 | Cybersecurity Advice, Cybersecurity News, Network Security, Web Filtering
There are some very good reasons why you should block file sharing websites. These websites are primarily used to share pirated software, music, films, and TV shows. It would be unlikely for the owner of the copyright to take action against an employer for failing to prevent the illegal sharing of copyrighted material, but this is an unnecessary legal risk.
However, the main risk from using these websites comes from malware. Research conducted by IDC in 2013 showed that out of 533 tests of websites and peer-2-peer file sharing networks, the downloading of pirated software resulted in spyware and tracking cookies being downloaded to users’ computers 78% of the time. More worryingly, Trojans were downloaded with pirated software 36% of the time.
A survey conducted on IT managers and CIOs at the time indicated that malware was installed 15% of the time with the software. IDC determined that overall there was a one in three chance of infecting a machine with malware by using pirated software.
Even visiting torrent sites can be harmful. This week Malwarebytes reported that visitors to The Pirate Bay were served malicious adverts. An advertiser used a pop-under to silently redirect users to a malicious site containing the Magnitude exploit kit which was used to downloaded Cerber ransomware onto users’ devices.
A study conducted by UC San Diego involved testing pirated software downloads using VirusTotal. VirusTotal checks files against the databases of 47 different anti-virus engines. The research team determined that 50% of pirated files were infected with malware.
Dealing with malware from pirated software was determined to take around 1.5 billion hours per year. For businesses the cost can be considerable. IDC calculated the cost to enterprises to be around $114 billion in 2013 alone. And that was just for the clean-up. The cost of data breaches caused by illegal software installations was estimated to be in the order of $350 billion.
Time to Block File Sharing Websites?
Organizations can monitor devices and check for unauthorized software installations on individual devices; however, by the time a software installation has been discovered, malware is likely to already have been installed. A recent report by Verizon suggests that on average, hackers are able to exfiltrate data within 28 minutes of gaining access to a system.
One of the easiest ways to manage risk is to block file sharing websites such as P2P and torrent sites. A web filter can be easily configured to block file sharing websites and prevent them from being accessed. Many web filters can also be configured to block specific file types from being downloaded, such as keygens and other executables.
By blocking file sharing websites organizations can ensure that copyright-violating activities are prevented and malware risk is effectively managed. Furthermore, web filters can be used to block web-borne threats such as phishing websites, compromised webpages, spam and botnets, adware, malware, ransomware, and anonymizers.
The failure to block file sharing websites could turn out to be costly. It is far better to block potentially dangerous websites and online activities than to have to cover the cost of removing malware infections and dealing with data breaches.
Apr 28, 2016 | Cybersecurity Advice, Internet Security News, Network Security, Web Filtering
Organizations are investing in technology to ensure the perimeter defense are not breached; however, it is also important to address the risk of insider data breaches. According to a recent report from Forrester, internal incidents were responsible for more than half of data breaches suffered by firms. Cybercriminals have stepped up their efforts and are attacking organizations with increased vigor, but the report suggests more than half of data breaches are caused by employee errors, oversights, and negligence.
Employees are under increasing pressure to get more work completed in less time. This can easily lead to errors being made or shortcuts being taken. Employees may be security minded most of the time, but it is all too easy for sloppy data security practices to creep in. Even with the most robust perimeter security defenses in place, simple mistakes can lead to disaster.
Email Borne Attacks Are Still A Major Risk
During the past 12 months the volume of spam email has fallen considerably. This is partly due to law enforcement taking down major botnets and the increasing use of efficient spam filters. Even with the reduced volume the threat from spam email is considerable. The Forrester report indicates spam email volume has dropped from almost 89% of all emails in 2014 to 68% of emails in 2015. However, over 91% of all spam emails contain a malicious link and 2.34% contain malicious email attachments.
Cybersecurity awareness training has helped to mitigate the risk of insider breaches to some degree but they are still occurring. Most employees now know not to open email attachments from people they do not know, but what about from people they do know?
There has been an increase in business email compromise attacks in recent months. These attacks involve the sending of spam and phishing emails from within an organization. These emails are more likely to result in malicious email attachments being opened and links being clicked than emails from strangers. All emails should be treated as suspicious and should be carefully checked, not only those from outside an organization.
Employees are aware never to run an executable file that has been sent via email and to be wary of opening zip files from strangers. The Forrester report suggests that attackers are increasingly using standard office files to infect their targets. Microsoft Office files are used in 44.7% of attacks.
Employees who install unauthorized software are also placing their companies at risk. The use of shadow IT is behind many data breaches. Cybercriminals are exploiting vulnerabilities in the software installed by end users. Many of these programs contain serious vulnerabilities.
How to Address the Risk of Insider Data Breaches
Tacking the threat from within is more complicated that securing the defense perimeter as it is far harder to prevent employees from making simple mistakes. Organizations must take steps to reduce the likelihood of mistakes being made, while also ensuring that when employees do make data security snafus do not prove to be catastrophic.
Some of the ways organizations can address the risk of insider data breaches include:
- Conduct background checks before hiring new staff
- Ensuring access to systems is terminated before staff are
- Limiting network privileges
- Block the copying of critical data onto portable devices
- Provide all new staff with data security training
- Regularly conducting refresher training sessions
- Conducting quarterly cybersecurity fire-drills to ensure training is not forgotten.
- Sending regular email bulletins to keep cybersecurity awareness training fresh in the mind
- Sending dummy phishing emails to staff to test the effectiveness of training
- Scanning for shadow IT installed on user devices
- Ensuring bank transfer requests are checked by two individuals before being authorized
- Using a web filtering service to block phishing websites and limiting access to potentially risky websites
- Configuring a web filter to block the downloading of risky file types
It may not be possible to eliminate the risk of insider data breaches, but it is possible to effectively mitigate risk.
Apr 22, 2016 | Cybersecurity Advice, Cybersecurity News, Web Filtering
The healthcare industry has had a hard time in recent months; however, it is far from the only industry being targeted by hackers. Manufacturing company cyberattacks are on the increase and the industry is now second only to healthcare according to a new report from IBM X-Force Research. The manufacturing industry has replaced the financial sector as hackers attempt to gain access to intellectual property. Intellectual property can be sold for big bucks on the black market.
$400 Billion Worth of Intellectual Property Is Stolen from U.S. Companies Every Year
According to figures from the Federal Bureau of Investigation, each year over $400 billion worth of intellectual property is stolen from the United States and sold overseas. Many of the attacks are conducted by nation-state backed hacking groups, although a number of players have now got in on the act due to the value of data and the relative ease of breaking through manufacturing company cybersecurity defenses.
According to the IBM’s 2016 Cyber Security Intelligence Index, manufacturers in the automotive sector were most frequently targeted. Chemical companies were the second most likely to be attacked. 30% of manufacturing company cyberattacks took place on automotive manufacturers.
Not only are the potential rewards for successful manufacturing company cyberattacks high, attacks are relatively easy to pull off. A successful attack on a company in the financial sector may be rewarding, but the defenses put in place to keep hackers at bay are usually far more robust than in less well regulated industries such as manufacturing. The manufacturing industry has been relatively slow to improve cybersecurity defenses.
Organizations in the healthcare industry are required to comply with the Health Insurance Portability and Accountability Act or HIPAA for short. HIPAA sets a number of minimum standards which must be met by all healthcare organizations. Administrative, technical, and physical safeguards must be implemented to keep patient data protected. The legislation has forced healthcare companies to improve their cybersecurity defenses.
Similarly, legislation has been introduced that requires organizations in the financial services industry to improve protections to keep data secure. Organizations must comply with the Gramm-Leach-Bliley Act and implement Payment Card Industry Data Security Standards. With no equivalent legislation covering the manufacturing industry, companies have not been forced to improve their cybersecurity defenses. While many organizations have implemented robust multi-layered security defenses, data security standards are higher in the healthcare and financial services verticals.
Many Manufacturing Company Cyberattacks Target Employees
With the number of manufacturing company cyberattacks increasing, cybersecurity defenses need to be improved. Many of the attacks target end users. Phishing and spear phishing emails can be a highly effective way of getting past security defenses. Employees are seen to be the weakest link in the security chain.
IBM X-Force senior threat researcher John Kuhn pointed out that servers are being targeted by hackers using phishing and spear phishing schemes. If employees can be lured onto malicious websites, vulnerabilities can be exploited and malware downloaded onto computers. From there it is a small hop to network servers.
Providing security training to staff is essential to reduce the risk of phishing attacks being successful. However, training alone is not sufficient to prevent all attacks. Software solutions should also be used to make it harder for end users to inadvertently install malware. A web filter should be implemented to prevent end users from downloading malicious software and visiting compromised websites. Web filtering can be a highly effective way of preventing attacks that target employees.
It is also essential to conduct comprehensive risk assessments to identify security vulnerabilities. All systems need to be assessed regularly. Any vulnerabilities identified need to be promptly addressed.
Apr 15, 2016 | Cybersecurity Advice, Internet Security News
Two new vulnerabilities in QuickTime for Windows have recently been discovered, but a patch to address the flaws will not be issued by Apple. Apple has taken the decision to depreciate QuickTime for Windows and has advised all Windows users to uninstall the software to prevent vulnerabilities from being exploited. Apple intends to keep supporting the OSX version.
The latest vulnerabilities in QuickTime for Windows (named ZDI-16-241 and ZDI-16-242) are both heap corruption remote code execution vulnerabilities, both of which allow an attacker to write data outside of an allocated heap buffer. The vulnerabilities could be exploited remotely, although user interaction is required. In order for an attacker to exploit these vulnerabilities the target would be required to open a malicious file or visit a malicious website.
One of the vulnerabilities affects the moov atom (ZDI-16-241) while the other (ZDI-16-242) involves a flaw with atom processing. Both could allow data to be written outside of an allocated heap buffer by providing an invalid index. This would allow code to be executed in the context of Windows QuickTime player.
Latest Vulnerabilities in QuickTime for Windows Require Uninstallation of the Software
The discovery of the new vulnerabilities in QuickTime for Windows spells the end of the software for Windows users. Apple, Trend Micro, and US-CERT have all advised Windows users to uninstall QuickTime ASAP in order to stay protected.
These two new vulnerabilities are unlikely to be the last to be discovered. Leaving the software installed will place users at risk of attack. Exploits for the new vulnerabilities are not believed to have been developed yet, and no active attacks are understood to have been conducted, but it is only a matter of time before the vulnerabilities are added to exploit kits.
Whenever a software developer takes the decision to stop supporting software it means users must find alternatives. IT departments should ensure that all Windows machines have QuickTime uninstalled as soon as possible.
Apple has decided to stop support for QuickTime for Windows as most media programs no longer use QuickTime to play common formats, while HTML 5 has rendered the browser add-on obsolete.
To uninstall QuickTime for Windows, conduct a search for the uninstaller – search for “uninstall QuickTime” – or remove the program via the Windows Control Panel. Apple advises users to save the registration key if using QuickTime 7 Pro, which can be found in the “Register” tab of the program (Click Edit > Preferences).
Apr 8, 2016 | Cybersecurity Advice, Cybersecurity News, Internet Security News
The dramatic rise in business email scams in the past 12 months has prompted the Federal Bureau of Investigation (FBI) to issue a new warning. Companies of all sizes are being targeted with business email compromise scams which relieve companies of tens of thousands if not hundreds of thousands or millions of dollars.
The FBI warns that scammers are now going to extraordinary lengths to fool company employees into making transfers of large sums of company funds into hacker’s accounts. These attacks are far from the random email spam campaigns typically associated with email scammers. Companies are extensively researched, individual targets are identified, and carefully crafted emails are sent. A variety of social engineering techniques are employed to convince an individual in the company to make a sizeable bank transfer to the attacker’s account.
There are two main variants of these business email scams. The first involves gaining access to the email account of the CEO or a senior executive in the company. This is usually achieved with a spear phishing campaign. This phase of the attack involves researching the company and identifying a target. That target is then sent a spear phishing email in order to gain access to their email login credentials.
Once access to an email account has been gained, emails are checked to determine the style of writing used by that individual – How they sign their emails, the terminology they use, and the level of familiarity they have with the second target: An individual that manages money or makes bank transfers for the company.
An email is then sent from the executive’s email account requesting a transfer be made. Account details are supplied with a reason for urgency, and an explanation of why the request is being made.
Since the emails come from a known source within the company, and the terminology and style of the email matches those typically received by the accounts department, the transfer is often made without being queried.
Another variation on the same theme does not require access to an email account. Instead a domain name is purchased that is virtually identical to that used by the target company, often with just two letters transposed. Typically, an L in the domain name is replaced with the numeral 1, or the letter O with a zero. Goog1e.com instead of google.com for example.
These business email scams are highly effective because they take advantage of employees’ reluctance to query requests from authority figures in their organization. The emails are also crafted so as not to arouse suspicion.
Business Email Scams Have Netted Criminals Over $2.3 Billion in Three Years
Over the past three years the FBI has received complaints about business email scams from over 79 countries, and from every state in the U.S. Recently attacks have spiked in Phoenix, with other U.S. cities also targeted. Between October 2013 and February 2016, the FBI has been informed of 17,642 victims of these attacks. Over $2.3 billion in losses have been reported.
However, recently the situation has become dire. There has been a 270% increase in business email scams since January 2015, and the amounts lost in each successful attack are substantial. FBI reports that in Arizona the typical transfers requested are between £$25,000 and $75,000. With such high rewards for criminals it is no surprise that so many attacks are being conducted.
The FBI has urged companies to exercise caution and to be on high alert for these business email scams. The advice provided is to be extremely wary of any email-only request for a wire transfer, even if it comes from within the company.
To prevent these attacks, accounts department staff should verify a transfer request with the individual by phone – never by email – and should check the email address of the sender carefully. Multi-level authentication of bank transfers should also be consider3ed to reduce the risk of a successful attack.
Mar 31, 2016 | Cybersecurity Advice, Network Security, Social Media, Web Filtering
There are a number of ways for managed service providers to increase cash flow and boost profits. Efficiency can be improved, staff productivity can be increased, better margins achieved, and new in-house products could be developed. Unfortunately, all of these are easier said than done.
The main ways to increase profits by a significant amount is to attract new customers and increase the amount each existing client is spending.
If only there was a secret ingredient that MSPs are missing that could help them help to win more business and get each client to spend more! The good news is that for many MSPs, there is such a product.
Any MSP that has yet to include a web filtering service into their product portfolio could be missing out on substantial profits.
Web Filtering – An Easy Way for MSPs to Increase Profits
Filtering the Internet is now essential for many enterprises. In certain Industries it is mandatory for companies to filter the Internet. They need to ensure sensitive data are protected and risk is effectively managed. Networks must be protected from attacks by hackers and with an increasing number of web-borne threats, Internet usage policies alone are not sufficient to keep organizations protected. Those policies need to be enforced and a web filter is the natural choice.
In some industries, education for example, it is mandatory for the Internet to be filtered. Minors must be prevented from accessing obscene website content or other material that could be harmful. Even when it is not mandatory to filter the Internet it is often desirable. Hotels, restaurants, transport networks, airports, cafes, and coffee shops are choosing to implement controls to ensure all users enjoy a safe browsing experience.
In business, productivity losses from Internet abuse can be considerable. If every employee wasted an hour each day on personal Internet use, the losses to a medium-sized company would be substantial. Some studies suggest even more time is wasted by employees each day on non-work related Internet activities.
Failure to filter the Internet can prove costly in many ways. For example, the accessing of adult content in the workplace can lead to the development of a hostile working environment, which affects morale, productivity, and can cause all manner of HR headaches. The use of torrent sites and the downloading of pirated films, music, TV shows, and software can cause organizations legal headaches as well as placing pressure on bandwidth.
Many websites are unsafe and accessing those sites places organizations at a greater risk of a malware infection. A single compromised computer can cause an incredible amount of damage. The latest ransomware attack on Medstar Health is a good example. A computer virus was inadvertently downloaded which resulted in the shutdown of the health system’s email for its entire workforce, as well as its electronic medical record system.
Hollywood Presbyterian Medical Center was attacked with ransomware and had to pay $17,000 to obtain security keys to unlock its data. It is not only healthcare organizations that are having to deal with ransomware. U.S Police Departments have been forced to pay attackers after their computers have been locked by file-encrypting software, and many organizations have fallen victim to ransomware, keyloggers, viruses, and other malicious software. These infections are a drain on productivity and take a considerable amount of time and resources to fix.
A web filtering solution can protect against web-borne threats, can be used to tackle productivity losses, and prevent illegal or unsuitable website content from being accessed. Web filtering is now less of an option for many businesses and more of a requirement. MSPs offering such a service can fine it is an easy sell and a great way to boost profits.
What to Look for in a Web Filtering Product
In order for a third-party product to be included in an MSPs existing portfolio it should have a number of features. MSPs therefore need to find a web filtering product that:
- Has generous margins
- Is easy for sales teams to sell to clients
- Has a low management overhead
- Is easy to install
- Appeals to a wide range of clients
- Can be easily incorporated into existing product offerings
- Can be easily incorporated into back-office systems
There is a product that ticks all of these boxes, and that is WebTitan Cloud.
WebTitan Cloud and WebTitan Cloud for WiFi – Ideal Web Filtering Solutions for MSPs
WebTitan Cloud is a 100% cloud-based DNS filtering solution that has been designed to be easy to implement, maintain, manage, and sell to clients. WebTitan Cloud a no-brainer for many organizations, allowing thousands of dollars to be saved.
WebTitan Cloud can help organizations increase productivity of the workforce, improve security posture to prevent malware infections, and highly competitive pricing means considerable savings can be made by organizations looking to switch web filtering providers.
WebTitan can be implemented without any effect on Internet speed, there is no need for any additional hardware, no software downloads are required. Our product is easy to use and management is straightforward and not labor-intensive.
Key Features and Benefits of WebTitan Cloud that will Appeal to MSPs
WebTitan Cloud and WebTitan Cloud for WiFi have been developed to be appealing to MSPs and their clients. To make it as easy as possible for our web filtering solutions to be incorporated into existing client packages and allow MSPs to boost profits, we offer the following:
White labelling – Allows MSPs to add their own branding and color schemes.
Hosting choices – We can host on our servers, provide private cloud hosting, or you can run our solution within your own infrastructure.
Generous margins for MSPs and highly competitive pricing – An easy way to boost profits.
Usage-based Monthly billing – Makes WebTitan Cloud more affordable for clients.
Flexible pricing – Our product can easily be included in your pricing models.
Multi-tenanted solution – Advanced customer management features makes it easy to add new clients.
API-Driven – Easy integration into back-end billing and reporting systems.
Highly scalable – Our web filtering solution is suitable for businesses of all sizes.
Excellent Support – Industry leading customer service and technical support. If you have a problem, it will be rapidly resolved.
To find out more about how easy it is to incorporate WebTitan Cloud into your existing portfolio and boost profits contact our sales team today.
Mar 25, 2016 | Cybersecurity Advice, Cybersecurity News, Network Security
Web-borne attacks on enterprises are increasing, although it is important not to forget to protect against email attacks, as shown by a recent campaign using the Olympic Vision keylogger.
Olympic Vision Keylogger Used in Recent Business Email Compromise Attacks
The attackers behind the latest campaign are using the Olympic Vision keylogger to gain access to business email accounts. Trend Micro discovered the latest campaign and was able to trace the attacks and link them to two Nigerian cybercriminals. Trend Micro determined that the current campaign has been conducted in 18 different countries including the United States.
Business email accounts contain a wealth of data, which in the wrong hands, could result in considerable damage being caused to an enterprise. However, it is not only data stored in the email accounts that hackers want to obtain. The cybercriminal gang behind the latest attacks have a different purpose. Attacks are being conducted to gain access to business email accounts to use them to send emails to account department employees instructing them to make bank transfers to the attackers’ accounts. Large transfers are often made following a business email compromise (BEC) attack.
If hackers can gain access to the email account of a senior executive, they can use that account to send messages to members of staff in the accounts or billing departments requesting transfers be made to their bank accounts. BEC is a highly effective attack strategy. If an email is sent from a CEO to the accounts department requesting an urgent transfer be made, many employees would not think twice before making the transfer as instructed.
This social engineering technique takes advantage of the fact that many employees would not question a direct request from a CEO or senior account executive. A transfer is made and the attacker receives the funds, withdraws the money, and closes the account. This often occurs before any red flags are raised, even when the transfer is for tens or hundreds of thousands of dollars.
Sophisticated Attacks Being Conducted Using Unsophisticated Malware
The Olympic Vision keylogger is not a sophisticated malware. Once installed on a device it will steal information including the computer name, Windows product keys, keystrokes, network information, clipboard text, and data saved in browsers, messaging clients, FTP clients, and email clients. It is also capable of taking screenshots.
Those data are then encrypted and are sent via email, FTP, or other means to the attacker. The Olympic Vision keylogger is capable of displaying fake error messages, and can disable computer functions to evade detection – Task Manager for example can be blocked as can registry editing tools. The Olympic Vision keylogger is capable of terminating programs that may detect it, and uses anti-emulation to prevent it running in a sandbox.
With the information collected, attackers are not only able to gain access to business email accounts, they can search for other computers, study workflows, and gather intelligence. The intel is used to construct convincing emails and ensure they are sent to individuals in the account department authorized to make bank transfers.
The attacks can be incredibly lucrative. The FBI reported recently that BEC attacks have been used by cybercriminals to obtain around $800 million dollars from businesses in the past year.
How to Protect Against BEC Attacks
There are a number of strategies that can be used to prevent BEC attacks from taking place. Software solutions can be used to prevent malware such as the Olympic Vision keylogger from being installed. SpamTitan spam filtering software can be used to block emails containing malicious attachments to prevent them from being sent to end users. If malicious emails are blocked, this places less reliance on end users not to open infected email attachments. SpamTitan can also block phishing emails, which are also used to gain access to login credentials via links to malicious websites.
Staff training is also essential. End users should receive basic security training and be advised of best practices to adopt to reduce risk. With software solutions and a culture of security awareness, the majority of attacks can be prevented.
However, it is also essential to introduce policies and procedures to prevent fraudulent bank transfers being made. A wise precaution is to introduce policies that require bank transfer requests to be authorized by a supervisor. This additional control can help to ensure fraudulent transfer requests are identified.
Any atypical request for a transfer from a senior account executive, especially those that require large sums to be transferred to accounts not previously used by the company, should be verified with the person who made the request prior to the transfer being made.
Mar 17, 2016 | Cybersecurity Advice, Cybersecurity News, Social Media, Web Filtering
Enterprise social media usage policies have only been introduced by 54% of organizations according to a recent social media research study conducted by Osterman Research.
Social media use in the workplace has grown significantly in recent years, both personal use of social media sites as well as the use of the platforms for business purposes. However, just over half of enterprises have implemented policies that limit or restrict use of the websites.
Enterprises face a choice. Allow the use of the sites and accept that a considerable amount of each employee’s day will be devoted to personal social media site use, or place controls to limit use. These can be restrictions on the times that the sites can be accessed, the amount of time each employee is “allowed” to take as Facetime, or the actions that can be performed on social media sites.
There are good reasons for not introducing social media usage policies. Some employers believe social media site use can improve collaboration between employees and departments. Some employers believe social media use can help improve corporate culture and even lead to faster decision making capabilities.
However, some studies suggest that employers lose more than an hour each day per employee to social media networks. If that figure is multiplied by the 500 or more employees in an organization, it represents a considerable productivity loss.
Many employers do not mind a little time on social media sites each day, provided that usage is kept within reasonable limits. An employee cannot be expected to work productively for a full 8 hours a day, so allowing some social media time can help employees recharge before they get back to working at full speed. If an employee takes 5 minutes every hour to check their Facebook feed, it could actually help to increase the work that they perform each day.
Social Media Usage Policies Can Help Employers Manage Security Risk
Use of social media platforms is not only about time not spent working. There is a security risk associated with the use of social media networks. That security risk is considerable and the risk is growing. The Osterman Research study revealed the risk of malware delivery via social media networks is considerable. 18% of respondents said that they had had malware installed as a result of social media site use. 25% said they had experienced a malware attack where they could not determine the origin. Some of those incidents may have also resulted from social media site use.
Social media site use may have benefits, but it is important for enterprises to manage the risks. To do that, social media usage policies are likely to be required along with technological controls to help enforce those policies.
Osterman Research suggested a three step approach should be taken. Before enterprises implement social media usage policies it is important to find out why social media platforms are being used and how often they are being accessed. An audit should be conducted to determine the extent to which sites are accessed, the tools that are being used by employees, the time spent on the sites, and the activities that take place.
This will allow organizations to determine the benefits they get from social media site use and weigh these up against the risks. Appropriate social media usage policies can then be developed.
Employees will need to be trained on appropriate social media usage. Employers have the right to monitor Internet activity at work. The use of Facebook, Twitter, LinkedIn and other social platforms is therefore not private. Employers should explain that they have the right to monitor social media usage at work and take action against individuals who violate social media usage policies.
Osterman suggests that technologies should be implemented to control social media usage to help mitigate the risk of malware downloads and other social media threats.
Controlling Social Media Usage at Work
WebTitan Gateway – and WebTitan Cloud for WiFi – can help in this regard. Both web filtering solutions can help organizations control the use of social media sites at work and both solutions can be used to enforce social media usage policies. Controls can be placed on when social media sites can be accessed: Outside working hours or during lunch hours for example. Controls can also be set by user group. The marketing department will require a different set of rules to the billing department for example.
Controls can also be implemented to manage risk from malware. The downloading of risky files can be blocked: .exe, .scr, .zip, or .bat for example. Links to malicious websites are often uploaded to social media networks. WebTitan can be configured to prevent those sites from being accessed. WebTitan also allows Internet usage to be carefully monitored.
Many organizations prefer to take a reactive approach to social media use at work, and only introduce controls when there has been a malware attack, a breach of confidentiality, or when site usage has reached unacceptable levels. Taking a more proactive approach can prevent problems before they occur.
Mar 10, 2016 | Cybersecurity Advice, Network Security, Web Filtering
Ransomware is not new; however, cybercriminals have been using the malicious software with increased frequency in recent months as a sure fire way of generating income. It is now essential to protect networks from ransomware due to the increased risk of attack.
What Is Ransomware?
Ransomware can be considered to be rogue security software. It uses the same encryption that companies are advised to use to protect their data from cyberattackers. It encrypts files to prevent them from being used or accessed. Encrypted files can only be unlocked with a security key. Attackers lock data and demand a ransom to provide the security key. Without the key, the files will remain locked forever. It is therefore important for organizations to take steps to protect networks from ransomware. The threat of attack is increasing and failure to take proactive steps to reduce risk could prove costly.
Why are Ransomware Infections Increasing?
Malware can be used to record keystrokes and gain login credentials to access bank accounts, or to create botnets that can be sold as a service. Corporate secrets can be sold to the highest bidder, or Social Security numbers, names, and dates of birth stolen and sold on to identity thieves. However, attacks of this nature take time and effort. Ransomware on the other hand gives criminals the opportunity to make a quick buck. Several hundred of them in fact.
If a cybercriminal can infect a single machine with ransomware and lock that device, a ransom of between $300 to $500 can be demanded. The ransom must be paid using the virtually anonymous Bitcoin currency. Bitcoin can be bought, sold, traded, and spent without having to disclose any identifying information. Cybercriminals are able to demand ransoms with reasonable certainty that they will not be caught.
Ransomware-as-a-service is being offered on underground networks, meaning cybercriminals do not need to be skilled hackers or programmers. For a payment of between 5% to 20% of the profits and a nominal download fee, criminals are able to use the malware to generate a significant income.
Ransomware is lucrative. One of the most sophisticated strains of ransomware, CryptoWall, has been estimated to have netted its developers around $325 million in profit. Considerably more in fact, since the CyberThreat Alliance figures were calculated in 2015.
It is not difficult to see the attraction of ransomware. Because of the effectiveness of ransomware campaigns, we are only likely to see even more infections in 2016. In fact, this year there have been a number of ransomware infections reported by companies who have failed to protect networks from ransomware infections, leaving them little alternative but to pay to have their data unlocked. The victims include schools, healthcare providers, and even law enforcement departments. All organizations need to protect networks from ransomware or they may be left with little choice but to pay a ransom to unlock their files.
Who Is Being Targeted with Ransomware?
In the majority of cases, individuals and businesses are not actually targeted. Ransomware is sent out randomly via spam email. Oftentimes, millions of emails are sent in a single campaign. It is a numbers game and a percentage of emails will be opened, a smaller number of machines will be infected, and organizations that have failed to protect networks from ransomware are likely to have to pay the ransom.
However, businesses are also being targeted by attackers as the money that can be demanded to unlock devices – and networks – is much higher. A business may decide to pay several thousand dollars to recover critical data. Hackers and cybercriminals know this and are targeting organizations with spear phishing emails designed to get users to visit malicious websites that download ransomware. Spam emails are also sent with the malware disguised as invoices or even image files.
How Much Are Cybercriminals Asking to Unlock Encrypted Devices?
While single users receive $500 demands, the same cannot be said of businesses. Attackers can demand whatever fee they want. In February, Hollywood Presbyterian Hospital felt that paying a $17,000 ransom was the most logical solution considering the cost of data loss, downtime, and the restoration of its systems. The effort required and the cost of rectifying an infection could exceed the ransom cost by several orders of magnitude.
Horry County school district in South Carolina paid a ransom of $8,500 to decrypt 25 servers. The FBI investigated and told the school it had no alternative but to pay the ransom if it wanted to recover its data. In 2015, the Tewkbury, Mass., Police Department was also forced to pay up after it suffered a CryptoLocker attack. While data could be restored from a backup, the most recent file was corrupted and the only viable backup was more than 18 months old. In late February, 2016., Melrose Police Department, Mass., also paid a ransom to unlock files.
Is There an Alternative to Paying A Ransomware Ransom?
Depending on the type of ransomware used by cybercriminals in their attack, it may be possible to unlock data without paying a ransom. In some cases, data may not actually be locked at all. Users may just be fooled into thinking that it is.
Scareware is used to fool users into thinking they have been attacked with ransomware, when in actual fact they have not. Paying the ransom will remove the scareware from the device, but since no files have been encrypted, it is possible to remove the malware without paying the ransom. Many security tools can be used. In fact, that is how the attackers often make their money. By selling victims a security tool to remove their own infection.
Kovtar ransomware is a little different. This malware locks a computer and displays a message that cannot be removed. A lock screen is used which is displayed on boot, which prevents the user from using their device. It resides in the registry, but can be removed without paying a ransom. It has been commonly used as a police scam, claiming the user had visited websites displaying child pornography, even though in all likelihood they did not. It displays an FBI or police department warning, and demands that a payment be made to avoid any further action.
However, ransomware that actually encrypts files is a different beast entirely. Encryption cannot be unlocked without a security key, although it may be possible to restore files from a backup or with a system restore. Provided of course that those files have not also been encrypted. Some ransomware encrypts the files needed to restore data from a backup, or the backup files themselves.
When files have been encrypted, even the FBI has advised individuals to pay the ransom. In 2015, Joseph Bonavolonta, FBI cybercrime chief in Boston, was quoted as saying, “To be honest, we often advise people just to pay the ransom.”
The FBI says that most ransomware attackers are true to their word and supply the keys. That is not necessarily the case though. The keys may not be supplied and the individual could receive a further demand. Some ransomware that has been tweaked has been broken, making it impossible to decrypt locked files. Paying the ransom in such cases would not allow data to be recovered. There is no guarantee that payment of a ransom will result in a working key being provided. It is therefore essential to implement a number of measures to protect networks from ransomware infections.
How to Protect Networks from Ransomware?
There are a number of strategies that can be adopted to protect networks from ransomware infections and to reduce the damage caused if security defenses are breached.
Perform Regular Backups
Performing daily and weekly backups is essential. This measure will not protect networks from ransomware, but it will reduce the damage cause if an infection occurs. Backups of data should ensure files can be recovered. However, backups cannot always be restored. Just as the Tewkbury Police Department. It is essential that backups are not stored on portable devices that are left connected to computers. Ransomware can encrypt portable drives and can scan and lock files on networks, not just on individual devices.
Use a Spam Filter
Ransomware is often spread via spam email. One of the best ways to protect networks from ransomware is to prevent spam email from being delivered. Using a robust spam filtering solution will ensure the majority of malicious emails are caught and quarantined to prevent them from being opened by end users.
SpamTitan blocks 99.9% of spam emails, greatly reducing the likelihood of employees infecting their computers and corporate networks with ransomware.
Train Staff How to Identify Malicious Emails
Staff training is essential and a great way of helping to protect networks from ransomware. Emails are occasionally delivered to inboxes even with a robust spam filter in place. Employees must therefore be made aware of the risk and taught best security practices to avoid compromising their network or infecting their devices. Employees should be told never to open an email attachment that has been sent from someone they do not know. They should always check the email address of the sender carefully. Unfortunately, ransomware is not only spread via spam emails and web-borne attacks are more difficult to identify.
Use WebTitan to Block Malicious Websites
Cybercriminals use malicious advertising – terms malvertising – to lure individuals onto malicious websites where drive-by ransomware downloads take place. These adverts are often placed on legitimate websites via third party advertising networks. Malicious links are also posted on social media networks. Phishing emails also contain links to malicious sites that download ransomware.
One of the best ways that businesses can reduce the risk of a web-borne attack and protect networks from ransomware infections is by limiting the websites that can be accessed via their Wi-Fi and hard-wired networks. Blocking websites known to contain malware, preventing the downloading of file types commonly associated with ransomware, and blocking third party adverts from being displayed can all greatly reduce risk. To do this, a web filter is required.
WebTitan Cloud for Wi-Fi and WebTitan Gateway can be used by businesses, schools, and operators of Wi-Fi networks to reduce the risk of a ransomware attack. WebTitan blocks users from engaging in risky online behaviors and visiting malicious websites. Regardless of the level of training provided to users of computer networks, it is not possible to eliminate risk entirely. Using a web filtering solution to protect networks from ransomware, along with staff training and a spam email filter can greatly improve security posture.
The cost of these protections for businesses, educational institutions, and healthcare organizations is likely to be far lower than the cost of paying a ransom.
Feb 21, 2016 | Cybersecurity Advice, Cybersecurity News, Social Media
Nothing is certain in life apart from death and taxes, apart from tax season phishing scams which have started particularly early this year. Inboxes are already being flooded with phishing emails as cybercriminals attempt to file tax returns early. Not their own tax returns of course, but fraudulent claims on behalf of any email recipient who divulges their Social Security number and personal data to the scammers.
Tax season phishing emails are sent out in the millions in the run up to the April 15, deadline. If a tax refund can be submitted before the victim, the criminals will receive the refund check.
How to Spot Tax Season Phishing Scams
Each year tax fraudsters develop new and ever more convincing phishing scams to get taxpayers to divulge their personal data and Social Security numbers. With these data, fraudsters can submit fake tax returns in the names of the victims.
While phishing emails can be easy to spot in some cases, the fraudsters are now getting much better at crafting official looking emails that appear to have been set from the IRS.
The emails use the same language that one would expect the IRS to use and the email templates use official logos. The emails contain links that have been masked to make the email recipient think they are being taken to an official website. Clicking on the link will fire up a browser window and the soon-to-be-victim will be taken to a website that looks official.
Visitors will be asked to update their personal information, add their Social Security number, or even be requested to divulge their Self-Select PIN for the online tax portal. Divulging these data is almost certain to result in tax fraud.
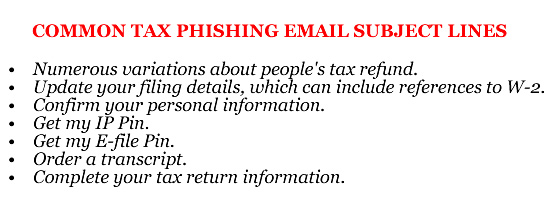
Tax Season Phishing Emails Are A Growing Concern
Taxpayers have been warned to be ultra-cautious. More tax season phishing scams have been identified this year than in previous years, with tax-related phishing and malware scams up 400% year on year.
IRS Commissioner John Koskinen warned that “Criminals are constantly looking for new ways to trick you out of your personal financial information so be extremely cautious about opening strange emails.”
Tax season phishing scams are not only conducted via email. In fact, phone scams have previously been one of the commonest ways that criminals obtain the information they need to submit fraudulent tax returns; however, the use of phishing emails is growing.
For the 2014 tax year, the IRS received 1,361 reports of phishing and malware schemes in the run up to the April deadline. That total has already been surpassed and February is not yet over. 1,389 reports have already been received. The January total was 254 higher than for the 2014 tax year, with 363 incidents reported by February 16, which is 162 more than the total for the entire month of February last year.
IRS Tax Season Phishing Emails Used to Deliver Malware
While criminals are attempting to phish for personal data, that is not the only consequence of clicking on a malicious link. The websites used by the cybercriminals behind these phishing scams are loaded with malware. Those malware enable cybercriminals to log keystrokes on infected computers and gain access to far more data than Social Security numbers. Bank account logins and passwords can be obtained, access to email accounts, and much more.
Tax Professionals Are Being Targeted with Phishing Scams
It is not only the public that must be vigilant and on the lookout for tax season phishing scams. Tax professionals are also being targeted by cybercriminals using similar schemes. The aim is to get accountants and tax advisers to reveal their online credentials such as their IRS Tax Professional PTIN System logins.
The IRS advice is to be vigilant and report any suspected phishing email. The IRS does not typically request data via email and does not initiate contact with taxpayers via email, text message, or social media channels. If an email is received asking for a link to be clicked or an attachment to be opened, it is likely to be a scam and should be reported to the IRS.
Feb 11, 2016 | Cybersecurity Advice, Internet Security News, Network Security, Web Filtering
One of the main priorities for IT professionals in 2016 is securing Wi-Fi hotspots. The use of unsecured public Wi-Fi is notoriously risky. Cybercriminals spy on the activity taking place at WiFi hotspots, and it is at these Internet access points is where many man-in-the-middle attacks take place.
The Dangers of Unsecured WiFi
Preventing employees from using personally owned and work devices on unsecured Wi-Fi networks is a major challenge, but one that must be met in order to keep work networks free from malware.
When employees use smartphones, tablets, and laptops to connect to unsecured Wi-Fi networks, there is a high risk that those devices may be compromised. Hotspots are frequently used to deliver malware to unsuspecting website visitors, and malicious software can subsequently be transferred to work networks. With personally owned devices increasingly used for private and work purposes, the risk of a work network malware infection is particularly high.
The risks associated with unsecured Internet access points are well known, yet people still tend to still engage in risky behavior when accessing the Internet via these wireless networks. In a rush to take advantage of free Internet access, basic security best practices are all too often ignored. Devices are allowed to connect to Wi-Fi hotspots automatically and Wi-Fi hotspots are not checked to find out if they are genuine or have been spoofed.
Security Professionals Concerned About Employees’ Use of Unsecured WiFi Networks
A recent survey conducted by the Cloud Security Alliance indicates security professionals are very concerned about the use of unsecured WiFi networks. The Cloud Security Alliance is a collective of security professionals, businesses, and privacy and security organizations that are committed to raising awareness of cybersecurity best practices.
The organization recently conducted a survey and asked 210 security professionals their opinions on the top threats to mobile computing in 2016. 2010 member organizations were polled and more than 8 out of 10 respondents (81%) said that the threat from unsecured WiFi access points was very real, and was one of the biggest mobile security risks in 2016.
The Importance of Securing WiFi Hotspots
Many organizations that operate a network of Wi-Fi hotspots have yet to implement security measures to keep users of those networks secure. Those Wi-Fi access points are made available to customers in bars, restaurants, hotels, airport lounges, sporting venues, and on public transport such as busses and trains.
Guests are allowed to connect to those networks, yet little is done to police the activity that takes place over the network. Consequently, the door is left open for cybercriminals to conduct attacks.
Failing to provide even a basic level of security is a big mistake. If patrons suffer malware infections, data loss, identity theft, or other forms of fraud as a result of accessing the internet at a particular location, they are likely never to return.
With IT professionals now educating their staff members about the dangers of using unsecured WiFi access points, businesses that offer secure WiFi access are likely to attract far greater numbers of customers than those that do not.
There is a cost associated with securing WiFi hotspots of course. However, what must be considered is the amount of business that will be lost as a result of not securing WiFi hotspots. The cost of implementing security measures is likely to be much lower in the long run.
Securing WiFi Hotspots with WebTitan Cloud for WiFi
A business offering customers wireless Internet access used to have to purchase additional hardware or software in order to secure WiFi access points. Not only was there a cost associated with adding a security solution, implementing that solution was a complex task that required skilled staff and many man-hours.
Providing a secure browsing environment for customers would mean getting them to download software to the device used to access the Internet. That is hardly a practical solution for a bar or restaurant where quick and easy access to the internet is required by customers.
WebTitan offers a much easier solution that makes securing WiFi hotspots a quick and easy task. Since WebTitan Cloud for WiFi is a 100% cloud-based security solution, it requires no additional hardware and no software installations. Any user can connect to a WiFi network and benefit from a secure browsing environment, regardless of the device they use to connect.
Setting up a WiFi web filtering security solution is also fast and painless, and doesn’t require much in the way of technical expertise. Simply change the DNS settings and point them to WebTitan, and a secure browsing environment will be available to customers in a matter of minutes.
Websites known to contain malware can be easily blocked, users can be prevented from downloading files types frequently associated with malware, and web content can be filtered to stop users from engaging in questionable internet activity such as viewing pornography. Securing WiFi hotspots couldn’t be any easier.
If you are interested in securing WiFi hotspots run by your company, contact WebTitan today to find out just how easy and cost effective it can be to offer your clients a secure browsing environment.
US Sales +1 813 304 2544
UK/EU Sales +44 203 808 5467
IRL +353 91 54 55 00
or email us at info@webtitan.com


